Last Updated: 20-DEC-2016
Update: The script for youtube also adding translate.google.com in the list too. workaround is to either edit the script, or make an ACCEPT rule before the deny rule, which should accept traffic going to translate.google.com ip addresses.
Recently I was providing mikrotikr related deployment support for an remote African 🌍 network where we configured hotspot for school students & the management wanted to block access to Facebook / Youtube & adult web sites for increased productivity.
Blocking adult websites was easy by redirecting DNS requests to OPENDNS but blocking facebook was a bit tricky because some people from the management wanted to have its access open for specific users. I preferred to have a address-list with the FB/YT server’s ip addresses using automated script.This way I have more control for these destinations for multi purpose. Example in Filter Rule I created DENY rule for traffic going to specific Destination list for all SOURCE address EXCEPT ALLOWED one.
Solution was to create two scheduled scripts which will pick facebook/youtube related dns entries from the Mikrotik DNS cache and add it in “facebook/youtube” address lists & we used these address list in the FILTER rule to either allow/block based on the source address list.
SCRIPT :
The below script(s) (which can be scheduled to run after every 5 or X minutes) will create a address list which will contain facebook/youtube server ips and afterwards an Firewall Filter rule will block request going to these destinations (using address list feature). To create this address list, it is required that your users must be using your mikrotik DNS as their primary dns , or make a dst-nat rule that forcefully route user dns (udp 53) requests to local mikrotik dns (forced dns redirection).
FOR FACEBOOK ~
# Script to add target web sites DNS IP addresses into address list
# Tested with Mikrotik 6.3x
# Syed Jahanzaib / aacable@hotmail.com
# List name
:local LISTNAME "facebook"
# Web site names which will be added in address list
:local TARGET1 "facebook.com"
:local TARGET2 "fbcd.net"
# 1st time runner, check if address list is not created previously and add entries in it for 1st time usage
:if ( [/ip firewall address-list find where list=$LISTNAME] = "") do={
:log warning "No address list for $TARGET1 and $TARGET2 found ! creating and adding resolved entry for 1st time usage ... zaib"
:resolve $TARGET1
:resolve $TARGET2
/ip firewall address-list add list=$LISTNAME
} else={
:log warning "Previous List for $LISTNAME found ! moving forward and checking if DNS entries can be added in it ..."
}
# Check DNS entries and collect matching names
:foreach i in=[/ip dns cache all find where (name~"$TARGET1" || name~"$TARGET2") && (type="A") ] do={
# Get IP Address from the names and hold it in temporary buffer
:local Buffer [/ip dns cache get $i address];
delay delay-time=10ms
# Check if entry is already not exists, then OK, otherwise ignore duplication
:if ( [/ip firewall address-list find where address=$Buffer] = "") do={
# Fetch DNS names for the entries
:local sitednsname [/ip dns cache get $i name] ;
# Print name in LOG window
:log info ("added entry: $sitednsname $Buffer");
# Add IP addresses and there names to the address list
/ip firewall address-list add address=$Buffer list=$LISTNAME comment=$sitednsname;
}
}
FOR YOUTUBE ~
# Script to add target web sites DNS IP addresses into address list
# Tested with Mikrotik 6.3x
# Syed Jahanzaib / aacable@hotmail.com
# List name
:local LISTNAME "youtube"
# Web site names which will be added in address list
:local TARGET1 "youtube.com"
:local TARGET2 "googlevideo.com"
# 1st time runner, check if address list is not created previously and add entries in it for 1st time usage
:if ( [/ip firewall address-list find where list=$LISTNAME] = "") do={
:log warning "No address list for $TARGET1 and $TARGET2 found ! creating and adding resolved entry for 1st time usage ... zaib"
:resolve $TARGET1
:resolve $TARGET2
/ip firewall address-list add list=$LISTNAME
} else={
:log warning "Previous List for $LISTNAME found ! moving forward and checking if DNS entries can be added in it ..."
}
# Check DNS entries and collect matching names
:foreach i in=[/ip dns cache all find where (name~"$TARGET1" || name~"$TARGET2") && (type="A") ] do={
# Get IP Address from the names and hold it in temporary buffer
:local Buffer [/ip dns cache get $i address];
delay delay-time=10ms
# Check if entry is already not exists, then OK, otherwise ignore duplication
:if ( [/ip firewall address-list find where address=$Buffer] = "") do={
# Fetch DNS names for the entries
:local sitednsname [/ip dns cache get $i name] ;
# Print name in LOG window
:log info ("added entry: $sitednsname $Buffer");
# Add IP addresses and there names to the address list
/ip firewall address-list add address=$Buffer list=$LISTNAME comment=$sitednsname;
}
}
SCHEDULER:
Schedule the script to run after every 5 minutes.
/system scheduler add disabled=no interval=5m name=facebook-script-run-schedule on-event=facebook policy=ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api start-date=feb/11/2014 start-time=00:00:00 add disabled=no interval=5m name=youtube-script-run-schedule on-event=youtube policy=ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api start-date=feb/11/2014 start-time=00:00:00
FILTER RULE:
Now create a FIREWALL FILTER rule which will actually DROP the request (in FORWARD CHAIN) going to facebook OR youtube address list.
[Make sure to move this rule on TOP , or before any general accept rule in Filter section)
/ip firewall filter add action=drop chain=forward comment=Filter Rule to block FB address LIST : ) disabled=no dst-address-list=facebook add action=drop chain=forward comment=Filter Rule to block YOUTUBE address LIST : ) disabled=no dst-address-list=youtube
[/sourcecode]
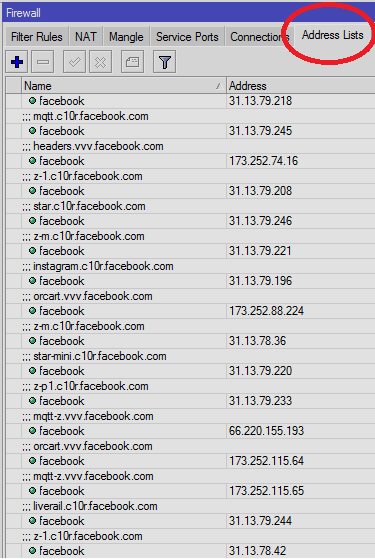
Now try to access the facebook, it may be open as usual, but as soon as the script will run, a address list will be created with the FB ip address list, & its access will be blocked.
As showed in the image below …
↓
TIP#1
TIME BASE FILTER RULE
You can also use this technique to block FB in some specific timings only. For example you want to block access to FB from 9am to 10:am then use the following filter rule.
/ip firewall filter add action=drop chain=forward comment=Filter Rule to block FB address LIST : ) disabled=no dst-address-list=facebook time=9h-10h,sun,mon,tue,wed,thu,fri,sat
TIP#2
Force / Redirect users to use your DNS
/ip firewall nat add action=redirect chain=dstnat comment="FORCE DNS TO LOCAL MIKROTIK DNS SERVER" dst-port=53 protocol=udp to-ports=53
TIP#3
Create Windows Update List using Scheduled Script (run every 5 minutes and fetch servers list from local dns cache) [Older post]
Note: Make sure your users are using mikrotik as there primary dns server
# Script to add target web sites DNS IP addresses into address list
# Tested with Mikrotik 6.4x
# Syed Jahanzaib / aacable@hotmail.com
# List name
:local LISTNAME "windowsupdateslist"
# Web site names which will be added in address list
:local TARGET1 "update.microsoft.com"
:local TARGET2 "download.windowsupdate.com"
:local TARGET3 "download.microsoft.com"
:local TARGET4 "windowsupdate.com"
:local TARGET5 "ntservicepack.microsoft.com"
:local TARGET6 "wustat.windows.com"
:local TARGET7 "stats.microsoft.com"
:local TARGET8 "mp.microsoft.com"
:local TARGET9 "ws.microsoft.com"
:local TARGET10 "sls.update.microsoft.com.akadns.net"
:local TARGET11 "vortex.data.microsoft.com"
:local TARGET12 "vortex-win.data.microsoft.com"
:local TARGET13 "fe2.update.microsoft.com.akadns.net"
:local TARGET14 "statsfe2.update.microsoft.com.akadns.net"
# 1st time runner, check if address list is not created previously and add entries in it for 1st time usage
:if ( [/ip firewall address-list find where list=$LISTNAME] = "") do={
:log warning "No address list for $TARGET1 found ! creating and adding resolved entry for 1st time usage ... zaib"
:resolve $TARGET1
/ip firewall address-list add list=$LISTNAME
} else={
:log warning "Previous List for $LISTNAME found ! moving forward and checking if DNS entries can be added in it ..."
}
# Check DNS entries and collect matching names
:foreach i in=[/ip dns cache all find where (name~"$TARGET1" || name~"$TARGET2" || name~"$TARGET3" || name~"$TARGET4" || name~"$TARGET5" || name~"$TARGET6" || name~"$TARGET7" || name~"$TARGET8" || name~"$TARGET9" || name~"$TARGET10" || name~"$TARGET11" || name~"$TARGET12" || name~"$TARGET13" || name~"$TARGET14") && (type="A") ] do={
# Get IP Address from the names and hold it in temporary buffer
:local Buffer [/ip dns cache get $i address];
delay delay-time=10ms
# Check if entry is already not exists, then OK, otherwise ignore duplication
:if ( [/ip firewall address-list find where address=$Buffer] = "") do={
# Fetch DNS names for the entries
:local sitednsname [/ip dns cache get $i name] ;
# Print name in LOG window
:log info ("added entry: $sitednsname $Buffer");
# Add IP addresses and there names to the address list
/ip firewall address-list add address=$Buffer list=$LISTNAME comment=$sitednsname;
}
}
Schedule above script in scheduler to run every few minutes. Then you can use this list to perform various functions like block them, or queue them by marking pkts. ZAIB
If this method helped you, please do let me know. your comments, tips for improvements etc are most welcome.
Regard’s
Syed Jahanzaib