From past few weeks we were having issues accessing our DVR systems from the Internet. The problem was that only when authentication dialogue appears, and after entering credentials , nothing appears further , no video nothing else, seems like connection going in sink hole.
As showed in the images below . . .
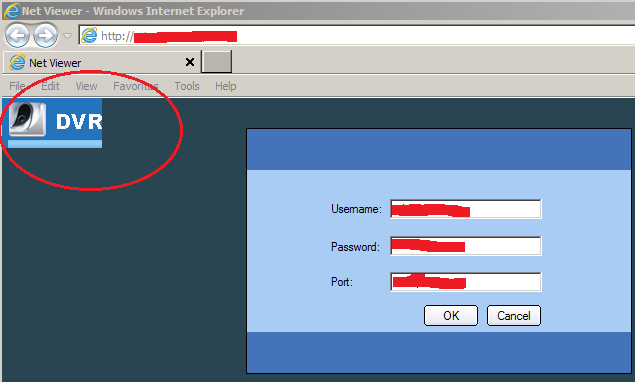
Login screen appear but with no background or complete logo
But after entering credentials, no video or any thing else came except for blank screen or with no video.
First we thought it might be something with the port forwarding , so first we did some investigation and found nothing, so called a Cisco Support personnel, and he also did some checking and found nothing.
Then we suspect our ISP and lounged complain regarding possible content filtering, but they claimed none of any traffic is filtered in corporate networks except VOIP.
We called the DVR support team and they claimed everything is fine at there DVR systems (nooobs :p)
Later on I configured an Mikrotik Routerboard in parallel just to verify that nothing is wrong with the Cisco ASA firewall.
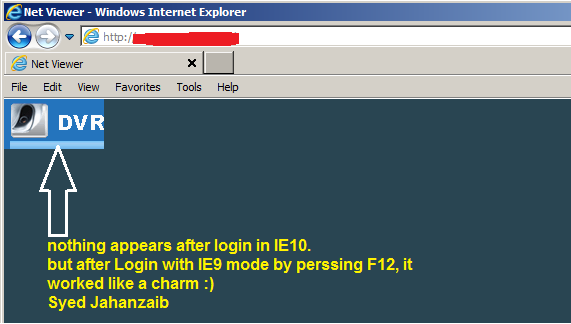
After searching on Google, I found out that it is something related to browser compatibility issues with the ACTIVEX component of the DVR manufacturer. But I was unable to sort it out completely. Luckily a friend from PORTUGAL (Mr. Rui Oliveria) confirmed me about the browser compatibility issue, and recommended me to run Browser (Internet Explorer 10) in IE9 mode. and ALHAMDOLILLAH it worked without any issue.
As showed in the image below . . .
.
Alternate way to launch Internet Explorer 10 in IE-9 mode via shortcut
To launch Internet Explorer 10 in IE9 mode, create a HTML file (you can use simple ntoepad to copy paste following code, and save it with IE9.html )
Copy paste the code from following pastebin location (WordPress is not good with pasting html codes)
Now double click this file and IE10 will be launch in IE9 mode. You can modify it as per your requirements.
.
You can use IETAB for Google Chrome & Firefox to view the DVR system.
.
Regard’s
Syed Jahanzaib

Aoa,
you have to forward 2 or 3 ports from modem
1- http that is 80 port
2- second is straming port by default its 554
3- This is control port and its vendor depended basically its acpi port, for HIKVISION its default is 8000
i suggest you to forward 554 port as well and it should work on all browsers without any tweak.
Thanks
Basit Khan
AMB NET SOLUTIONS
http://www.basitkhan.info
LikeLike
Comment by Basit Khan — November 28, 2013 @ 9:08 AM
Thank you for your TIP. unfortunately this DVR donot work with RTSP port which 554 by default. It uses only port 80 and 8001 TCP. We confirmed it several time by tracing from router, and by packet tracert WIRESHARK, Both are forwarded from the router to DVR but not working, We have another 3rd party IP base camera which uses port 80/800x/554 port and it works fine without any issue,, Only specific DVR have issues.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — November 28, 2013 @ 9:11 AM
Sir, mene apnay network mein dvr lagaya hai per wo bina hotspot login keye saray network per kahin bhi dvr k software k through access ho jata hai aur cams feed show ho jaty hai. kindly is ka koi solution bta dein takay sirf hotspot login ya pppoe authenticate honay k baad dvr access ho.
LikeLike
Comment by nasir — December 24, 2013 @ 6:10 PM
use PPOE dialer from your DVR instead of DHCP. hope this will fixed your problem !
LikeLike
Comment by Basit Khan — December 26, 2013 @ 10:28 AM
sir kuch dvr pppoe pe connect nhi hotay, masla ye hai k agar meray customers mein se koi bhi apna dvr hotspot pe lagata hai to wo saray city mein kahin bhi access ker leta hai kuyn k meray network ki coverage alomost city mein har jaga hai, hotspot to aik session hi create kerta hai per username, problem ye hai k agar dvr conected hai meray network se chaye login nhi howa phir bhi wo network access kerta hai is ko kesay block ker saktay hai takay sirf hotspot login honay k baad hi network access ho, shaihd ye dvr koi aisi port use kerta hai jesay hotspot block nhi kerta login se pehlay, sir kiya koi aisi firewall script hai jo hotspot pe login honay se pehlay sari ports ko block keray aur hotspot login page pe redirect keray or atleast block ker de? kindly help me, mene khud bhi check ker liya hai dvr laga k har jaga access ho jata hai.
LikeLike
Comment by nasir — December 26, 2013 @ 5:55 PM
shahzaib bhai mere mikrotik ke server mein trojan horse ka virus aa gaya hai usko kaise remove karna hai…
LikeLike
Comment by Shahab Khan — December 5, 2013 @ 5:13 PM
Just copy and paste these rules in Net Terminal,
It will keep your MkTik protect from various attacks
/ip firewall filter
add chain=icmp comment=”echo reply” icmp-options=0:0 protocol=icmp
add chain=icmp comment=”allow parameter bad” icmp-options=12:0 protocol=icmp
add chain=icmp comment=”net unreachable” icmp-options=3:0 protocol=icmp
add chain=icmp comment=”host unreachable” icmp-options=3:1 protocol=icmp
add chain=icmp comment=”allow source quench” icmp-options=4:0 protocol=icmp
add chain=icmp comment=”allow time exceed” icmp-options=11:0 protocol=icmp
add chain=icmp comment=”allow echo request” icmp-options=8:0 protocol=icmp
add action=drop chain=icmp comment=”deny all other types”
add action=drop chain=input comment=”drop ftp brute forcers” dst-port=21 \
protocol=tcp src-address-list=ftp_blacklist
add chain=output content=”530 Login incorrect” dst-limit=\
1/1m,9,dst-address/1m protocol=tcp
add action=add-dst-to-address-list address-list=ftp_blacklist \
address-list-timeout=3h chain=output content=”530 Login incorrect” \
protocol=tcp
add action=drop chain=input comment=”drop ssh brute forcers” dst-port=22 \
protocol=tcp src-address-list=ssh_blacklist
add action=add-src-to-address-list address-list=ssh_blacklist \
address-list-timeout=1w3d chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage3
add action=add-src-to-address-list address-list=ssh_stage3 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage2
add action=add-src-to-address-list address-list=ssh_stage2 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage1
add action=add-src-to-address-list address-list=ssh_stage1 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp
add action=drop chain=forward comment=”drop ssh brute downstream” dst-port=22 \
protocol=tcp src-address-list=ssh_blacklist
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”Port scanners to list ” \
protocol=tcp psd=21,3s,3,1
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”NMAP FIN Stealth scan” \
protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”SYN/FIN scan” protocol=tcp \
tcp-flags=fin,syn
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”SYN/RST scan” protocol=tcp \
tcp-flags=syn,rst
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”FIN/PSH/URG scan” protocol=\
tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”ALL/ALL scan” protocol=tcp \
tcp-flags=fin,syn,rst,psh,ack,urg
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”NMAP NULL scan” protocol=tcp \
tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
add action=drop chain=input comment=”dropping port scanners” \
src-address-list=”port scanners”
add action=drop chain=forward comment=”dropping port scanners” \
src-address-list=”port scanners”
add action=drop chain=input comment=”Drop Invalid connections” \
connection-state=invalid
add chain=input comment=”Allow Established connections” connection-state=\
established
add action=drop chain=forward comment=”drop invalid connections” \
connection-state=invalid
add chain=forward comment=”allow already established connections” \
connection-state=established
add chain=forward comment=”allow related connections” connection-state=\
related
add action=drop chain=forward comment=”Block Bogon IP addresses” src-address=\
0.0.0.0/8
add action=drop chain=forward dst-address=0.0.0.0/8
add action=drop chain=forward src-address=127.0.0.0/8
add action=drop chain=forward dst-address=127.0.0.0/8
add action=drop chain=forward src-address=224.0.0.0/3
add action=drop chain=forward dst-address=224.0.0.0/3
add action=jump chain=forward comment=”Make jumps to new chains” jump-target=\
tcp protocol=tcp
add action=jump chain=forward jump-target=udp protocol=udp
add action=jump chain=forward jump-target=icmp protocol=icmp
add action=drop chain=tcp comment=”deny TFTP” dst-port=69 protocol=tcp
add action=drop chain=tcp comment=”deny RPC portmapper” dst-port=111 \
protocol=tcp
add action=drop chain=tcp comment=”deny RPC portmapper” dst-port=135 \
protocol=tcp
add action=drop chain=tcp comment=”deny NBT” dst-port=137-139 protocol=tcp
add action=drop chain=tcp comment=”deny cifs” dst-port=445 protocol=tcp
add action=drop chain=tcp comment=”deny NFS” dst-port=2049 protocol=tcp
add action=drop chain=tcp comment=”deny NetBus” dst-port=12345-12346 \
protocol=tcp
add action=drop chain=tcp comment=”deny NetBus” dst-port=20034 protocol=tcp
add action=drop chain=tcp comment=”deny BackOriffice” dst-port=3133 \
protocol=tcp
add action=drop chain=tcp comment=”deny DHCP” dst-port=67-68 protocol=tcp
add action=drop chain=udp comment=”deny TFTP” dst-port=69 protocol=udp
add action=drop chain=udp comment=”deny PRC portmapper” dst-port=111 \
protocol=udp
add action=drop chain=udp comment=”deny PRC portmapper” dst-port=135 \
protocol=udp
add action=drop chain=udp comment=”deny NBT” dst-port=137-139 protocol=udp
add action=drop chain=udp comment=”deny NFS” dst-port=2049 protocol=udp
add action=drop chain=udp comment=”deny BackOriffice” dst-port=3133 protocol=\
udp
LikeLike
Comment by Basit Khan — December 6, 2013 @ 1:11 PM
Just Copy and Past these rules into New Terminal,
This will protect your Box from various attacks.
/ip firewall filter
add chain=icmp comment=”echo reply” icmp-options=0:0 protocol=icmp
add chain=icmp comment=”allow parameter bad” icmp-options=12:0 protocol=icmp
add chain=icmp comment=”net unreachable” icmp-options=3:0 protocol=icmp
add chain=icmp comment=”host unreachable” icmp-options=3:1 protocol=icmp
add chain=icmp comment=”allow source quench” icmp-options=4:0 protocol=icmp
add chain=icmp comment=”allow time exceed” icmp-options=11:0 protocol=icmp
add chain=icmp comment=”allow echo request” icmp-options=8:0 protocol=icmp
add action=drop chain=icmp comment=”deny all other types”
add action=drop chain=input comment=”drop ftp brute forcers” dst-port=21 \
protocol=tcp src-address-list=ftp_blacklist
add chain=output content=”530 Login incorrect” dst-limit=\
1/1m,9,dst-address/1m protocol=tcp
add action=add-dst-to-address-list address-list=ftp_blacklist \
address-list-timeout=3h chain=output content=”530 Login incorrect” \
protocol=tcp
add action=drop chain=input comment=”drop ssh brute forcers” dst-port=22 \
protocol=tcp src-address-list=ssh_blacklist
add action=add-src-to-address-list address-list=ssh_blacklist \
address-list-timeout=1w3d chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage3
add action=add-src-to-address-list address-list=ssh_stage3 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage2
add action=add-src-to-address-list address-list=ssh_stage2 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp src-address-list=ssh_stage1
add action=add-src-to-address-list address-list=ssh_stage1 \
address-list-timeout=1m chain=input connection-state=new dst-port=22 \
protocol=tcp
add action=drop chain=forward comment=”drop ssh brute downstream” dst-port=22 \
protocol=tcp src-address-list=ssh_blacklist
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”Port scanners to list ” \
protocol=tcp psd=21,3s,3,1
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”NMAP FIN Stealth scan” \
protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”SYN/FIN scan” protocol=tcp \
tcp-flags=fin,syn
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”SYN/RST scan” protocol=tcp \
tcp-flags=syn,rst
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”FIN/PSH/URG scan” protocol=\
tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”ALL/ALL scan” protocol=tcp \
tcp-flags=fin,syn,rst,psh,ack,urg
add action=add-src-to-address-list address-list=”port scanners” \
address-list-timeout=2w chain=input comment=”NMAP NULL scan” protocol=tcp \
tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
add action=drop chain=input comment=”dropping port scanners” \
src-address-list=”port scanners”
add action=drop chain=forward comment=”dropping port scanners” \
src-address-list=”port scanners”
add action=drop chain=input comment=”Drop Invalid connections” \
connection-state=invalid
add chain=input comment=”Allow Established connections” connection-state=\
established
add action=drop chain=forward comment=”drop invalid connections” \
connection-state=invalid
add chain=forward comment=”allow already established connections” \
connection-state=established
add chain=forward comment=”allow related connections” connection-state=\
related
add action=drop chain=forward comment=”Block Bogon IP addresses” src-address=\
0.0.0.0/8
add action=drop chain=forward dst-address=0.0.0.0/8
add action=drop chain=forward src-address=127.0.0.0/8
add action=drop chain=forward dst-address=127.0.0.0/8
add action=drop chain=forward src-address=224.0.0.0/3
add action=drop chain=forward dst-address=224.0.0.0/3
add action=jump chain=forward comment=”Make jumps to new chains” jump-target=\
tcp protocol=tcp
add action=jump chain=forward jump-target=udp protocol=udp
add action=jump chain=forward jump-target=icmp protocol=icmp
add action=drop chain=tcp comment=”deny TFTP” dst-port=69 protocol=tcp
add action=drop chain=tcp comment=”deny RPC portmapper” dst-port=111 \
protocol=tcp
add action=drop chain=tcp comment=”deny RPC portmapper” dst-port=135 \
protocol=tcp
add action=drop chain=tcp comment=”deny NBT” dst-port=137-139 protocol=tcp
add action=drop chain=tcp comment=”deny cifs” dst-port=445 protocol=tcp
add action=drop chain=tcp comment=”deny NFS” dst-port=2049 protocol=tcp
add action=drop chain=tcp comment=”deny NetBus” dst-port=12345-12346 \
protocol=tcp
add action=drop chain=tcp comment=”deny NetBus” dst-port=20034 protocol=tcp
add action=drop chain=tcp comment=”deny BackOriffice” dst-port=3133 \
protocol=tcp
add action=drop chain=tcp comment=”deny DHCP” dst-port=67-68 protocol=tcp
add action=drop chain=udp comment=”deny TFTP” dst-port=69 protocol=udp
add action=drop chain=udp comment=”deny PRC portmapper” dst-port=111 \
protocol=udp
add action=drop chain=udp comment=”deny PRC portmapper” dst-port=135 \
protocol=udp
add action=drop chain=udp comment=”deny NBT” dst-port=137-139 protocol=udp
add action=drop chain=udp comment=”deny NFS” dst-port=2049 protocol=udp
add action=drop chain=udp comment=”deny BackOriffice” dst-port=3133 protocol=\
udp
Thankx
LikeLike
Comment by Basit Khan — December 6, 2013 @ 1:13 PM
Thank You for your contribution 🙂
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 6, 2013 @ 1:39 PM
shukriya aap sab ka lekin yeh sab save kaise ho ga
LikeLike
Comment by Shahab Khan — December 9, 2013 @ 1:39 PM
NO need to save, just copy and paste these lines into New Terminal, it will save automatically
LikeLike
Comment by Basit Khan — December 10, 2013 @ 8:39 AM
but this is not working trojan horse is still in my server…
LikeLike
Comment by Shahab Khan — December 10, 2013 @ 10:00 AM
Bro, will you please let me know how you check that the trojan horse is still in server?
go to Winbox—>IP—>Firewall—->Address List and check that are there any list created dynamically?
It might be possible that the trojan is present into your local system rather than your server. coz there is nothing to do a Trojan in server because of Linux has permission attribute on each and every file of it,
furthermore the Mikrtoik server is closed source so they keep the root privileges and other user programs can’t change anything or any settings.
LikeLike
Comment by Basit Khan — December 11, 2013 @ 1:00 PM
no bro there is no list created but when i open login page on client computer which has installed avast 7.0 pro that says trojan has detected and blocked my login page….this is the problem
LikeLike
Comment by Shahab Khan — December 11, 2013 @ 3:49 PM
ooh i c, its the hotspot website error, just reset the html pages from Hotspot menu and then try again!
LikeLike
Comment by Basit Khan — December 11, 2013 @ 3:51 PM
kindly tell me how to reset because i am new in this field….thanks
LikeLike
Comment by Shahab Khan — December 11, 2013 @ 4:51 PM
reset what brother?
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 12, 2013 @ 8:35 AM
go to Winbox—>Ip—->Hotspot—>Servers—->Double click / Select your first profile in my case its (hotspot1)—->Reset Html
LikeLike
Comment by Basit Khan — December 12, 2013 @ 2:28 PM
you guys are very nice thanks for helping me..\
LikeLike
Comment by Shahab Khan — December 12, 2013 @ 2:58 PM
bhai koi aisa proxy ip jo youtube sahi open kare aur rukkay na download bhi ho aur isko hotspot mein kaise add karein gay
LikeLike
Comment by chillnmasty — December 15, 2013 @ 10:08 PM
Mera HK Vision ka DVR bahir say connect horahay hay Playback bhi show kar raha hay main recording dekh sakta hon bahir say apnay office kay CCTV ki bit live streaming nahin kar pa raha plz help?????? sari ports open hain meray office ki aik hi static IP hay wohi main CCTV kay lye use kar raha hon can anyone help plzzzz!!!
LikeLike
Comment by adnanmalikaaa — June 4, 2015 @ 6:14 PM
Sir i have a dvr in my home which is connected to my router via 70 meter long cat 6 cable. when we set these cabling and port forwarding in router it was working properly i can access dvr via lan but after 2-3 days its not working. I changed router 2 to 3 time but every router works only 2-3 days. .
when these same cable directly connected to my laptop i can access my dvr. it shows cabling is fine.
I think it might be a POE issue on router. currently i am using edimax br6228ns as my home router.
Do i need to install POE switch in between router and dvr ? or any home router that support 70 meter long lan cable. if yes then please provide device name model no.
please provide solution for above issue.
LikeLike
Comment by Shitesh — June 27, 2015 @ 6:05 PM
Sir any update regarding my above issue posted on { Comment by Shitesh — June 27, 2015 @ 6:05 PM }
LikeLike
Comment by shitesh — July 4, 2015 @ 5:07 PM