
I was stucked with a case (in K.S.A Tabook) regarding configuration for dual wan PCC using pppoe client as wan and pppoe serve for user end in one RB. I made this configuration last year but was unable to repeat it when it was required few days back.
I have a very short amount of brain memory , something like 16 KB only 🙂 So posting the export as a reference
Following is a short reference guide for Mikrotik base dual wan PCC (using pppoe clients) with PPPoE Server as a authentication server for local users in one Box. You can add as much wan (pppoe clients) as you like.
Make sure you change the interface name accordingly. In this example I have 3 interfaces.
ether0 (named as Local) is connected with Local LAN users.
ether 1 & 2 (named as WAN1 & WAN2) are connected with ISP WAN switch.
Also change the user name passwords in the pppoe client section, or create manually via PPP/Interfaces
PPPoE users IP pool is 172.16.0.0/16 (internet is allowed for this series only means when the user will be connected via pppoe dialer, he will be able to use internet)
SCRIPT:
# Setting up INTERFACES names for our comfort (Zaib) /interface ethernet set 0 name=Local set 1 name=WAN1 set 2 name=WAN2 ### Adding PPPoE Client connections for each WAN interface, Make sure to change it or add via GUI /interface pppoe-client add ac-name="" add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN1 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out1 password=hahaha \ profile=default service-name="" use-peer-dns=no user=user-1 add ac-name="" add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN2 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out2 password=hahaha \ profile=default service-name="" use-peer-dns=no user=user-2 ### Starting the MANGLE MAGIC : ) PCC SCRIPTING START Here (Zaib) /ip firewall mangle add action=accept chain=prerouting disabled=no in-interface=pppoe-out1 add action=accept chain=prerouting disabled=no in-interface=pppoe-out2 add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan1_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:2/0 src-address=172.16.0.0/16 add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan2_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:2/1 src-address=172.16.0.0/16 add action=mark-routing chain=prerouting connection-mark=wan1_conn disabled=no new-routing-mark=to_wan1 passthrough=yes src-address=172.16.0.0/16 add action=mark-routing chain=prerouting connection-mark=wan2_conn disabled=no new-routing-mark=to_wan2 passthrough=yes src-address=172.16.0.0/16 ### NATTING both WAN connection for PPPoE IP Pool users only /ip firewall nat add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out1 src-address=172.16.0.0/16 add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out2 src-address=172.16.0.0/16 ### Setting Default Routes for MARKED packets for both WAN and for local router use. (zaib) /ip route add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 routing-mark=to_wan1 scope=30 target-scope=10 add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 routing-mark=to_wan2 scope=30 target-scope=10 add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 scope=30 target-scope=10 add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=pppoe-out2 scope=30 target-scope=10
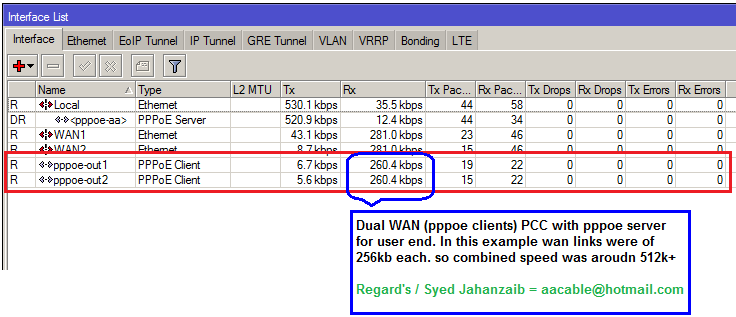
Some screenshots for the results.
▼▼▼
▲▲▲
Side Note: [had this issue at local cable.net who had DSL modems]
If you are facing difficulty in opening dsl modem page, then try following code.
/ip firewall address-list add list=exempt-from-pcc address=192.168.1.1/32 add list=exempt-from-pcc address=192.168.2.1/32 #(change ips to your adsl modem ip’s) /ip firewall mangle add chain=prerouting dst-address-list=exempt-from-pcc action=accept
Move above mangle rule to TOP (above all other rules in mangle) .Try and let me know.
☺
Regard’s
Syed Jahanzaib
I NEED WITH FIVE PPPOE CLIENT PCC CAN U DO IT FOR ME PLEASE.
LikeLike
Comment by Waqas Hussain — December 6, 2013 @ 7:36 PM
I NEED WITH FIVE PPPOE CLIENT PCC CAN U DO IT FOR ME PLEASE.
i am sorry i need to pcc with 9th pppoe clients… please jahanzaib bhai can u do that?
1 for the LAN and 9 pppoe clients for the pcc bandhwidht… please
LikeLike
Comment by Waqas Hussain — December 6, 2013 @ 7:38 PM
JAHANZAIB BHAI I CREATED THIS SCRIPT CAN U CHEK IT PLEASE IS THAT WILL BE WORKING SCRIPT OR NOT????
/interface ethernet
set 0 name=Local
set 1 name=WAN1
set 2 name=WAN2
set 3 name=WAN3
set 4 name=WAN4
set 5 name=WAN5
set 6 name=WAN6
set 7 name=WAN7
set 8 name=WAN8
set 9 name=WAN9
/interface pppoe-client
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN1 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out1 password=hahaha
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN2 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out2 password=hahaha
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN3 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out3 password=hahaha
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN4 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out4 password=hahaha
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN5 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out5 password=hahaha
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN6 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out6 password=hahaha
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN7 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out7 password=hahaha
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN8 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out8 password=hahaha
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN9 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out9 password=hahaha
/ip firewall mangle
add action=accept chain=prerouting disabled=no in-interface=pppoe-out1
add action=accept chain=prerouting disabled=no in-interface=pppoe-out2
add action=accept chain=prerouting disabled=no in-interface=pppoe-out3
add action=accept chain=prerouting disabled=no in-interface=pppoe-out4
add action=accept chain=prerouting disabled=no in-interface=pppoe-out5
add action=accept chain=prerouting disabled=no in-interface=pppoe-out6
add action=accept chain=prerouting disabled=no in-interface=pppoe-out7
add action=accept chain=prerouting disabled=no in-interface=pppoe-out8
add action=accept chain=prerouting disabled=no in-interface=pppoe-out9
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan1_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/0 src-address=10.100.50.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan2_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/1 src-address=10.100.50.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan3_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/2 src-address=10.100.50.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan4_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/3 src-address=10.100.50.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan5_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/4 src-address=10.100.50.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan6_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/5 src-address=10.100.50.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan7_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/6 src-address=10.100.50.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan8_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/7 src-address=10.100.50.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan9_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:9/8 src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan1_conn disabled=no new-routing-mark=to_wan1 passthrough=yes src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan2_conn disabled=no new-routing-mark=to_wan2 passthrough=yes src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan3_conn disabled=no new-routing-mark=to_wan3 passthrough=yes src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan4_conn disabled=no new-routing-mark=to_wan4 passthrough=yes src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan5_conn disabled=no new-routing-mark=to_wan5 passthrough=yes src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan6_conn disabled=no new-routing-mark=to_wan6 passthrough=yes src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan7_conn disabled=no new-routing-mark=to_wan7 passthrough=yes src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan8_conn disabled=no new-routing-mark=to_wan8 passthrough=yes src-address=10.100.50.0/24
add action=mark-routing chain=prerouting connection-mark=wan9_conn disabled=no new-routing-mark=to_wan9 passthrough=yes src-address=10.100.50.0/24
/ip firewall nat
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out1 src-address=10.100.50.0/24
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out2 src-address=10.100.50.0/24
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out3 src-address=10.100.50.0/24
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out4 src-address=10.100.50.0/24
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out5 src-address=10.100.50.0/24
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out6 src-address=10.100.50.0/24
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out7 src-address=10.100.50.0/24
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out8 src-address=10.100.50.0/24
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out9 src-address=10.100.50.0/24
/ip route
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 routing-mark=to_wan1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 routing-mark=to_wan2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 scope=30 target-scope=10
/ip route
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out3 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out4 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out5 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out6 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out7 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out8 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out9 scope=30 target-scope=10
LikeLike
Comment by Waqas Hussain — December 6, 2013 @ 8:32 PM
hopefuly it will work. are you using it only for pcc or pppoe server is also hosted in same box ?
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 6, 2013 @ 8:37 PM
HOW IS IT SUPPOSE TO WORK ??THERE IS MISSING RULES IN IP ROUTE IT’S NOT COMPLETED
LikeLike
Comment by ALI SAMEER — April 7, 2014 @ 1:05 PM
Hi Syed,
Can we use the External DHCP Server for PPPOE instead of Local Pool so that we can the reservation for particular users who has requested the static IP.
Thanks & Best Regards
RAJA SEKHAR B
Vice President – Internet Operations
+91 8886609828
LikeLike
Comment by RAJA SEKHAR — December 7, 2013 @ 12:32 PM
yes you can use external DHCP server,
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 9, 2013 @ 11:03 AM
helllo sir i am using mikroik hotspot and pppoe server ,,,but problem is when we conect wifi router browsing speed going slow ,,,when we conect directly with pc ,,i will be fine,,plz tell me any solution,,,if u have any pppoe and hosptot script then give me,,,,em w8tinb
LikeLike
Comment by zameer ahmed — February 5, 2015 @ 8:25 PM
Nice work with no doubt Syed jahanzaib and to tell you I forcibly tested it after i lost my pppoe server RB this sunday evening 😉 with no where to go and buy a new one. now i’m useing one RB loadbalancing pppoe clients with my pppoe server and your script works 100%, so after The Almighty thanks goes to you for this post, but as you know there is one thing remain>> we still have the Mk webproxy not working and we need as i read from your other posts to exclude port 80 from loadbalancing, many thanks again and we are looking foreword to fix that matter, have a great time.
LikeLike
Comment by Redheart — December 9, 2013 @ 6:02 AM
plz i want ur email
my mail yasser.alrewad@gmail.com
LikeLike
Comment by alrewad — December 9, 2013 @ 5:17 PM
mr. sayed
LikeLike
Comment by alrewad — December 9, 2013 @ 5:18 PM
d
LikeLike
Comment by alrewad — December 9, 2013 @ 5:19 PM
hi, how to check load balancing running in mikrotik thanks (mohamad basuki)
LikeLike
Comment by Mohamad Basuki — December 12, 2013 @ 11:40 AM
if you want to monitor if load balancing is working ok, try to download multiple files using any download software like IDM/DAP , and then monitor both wan usage. Both WAN links should be utilize in almost same manner (if the links are of same capacity and quality)
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 16, 2013 @ 10:47 AM
Hi, can you please provide the right way hot to create the pppoe server in mikrotik with above pppoe-client pcc method?
LikeLike
Comment by esalehnet — December 14, 2013 @ 12:03 AM
pppoe server is simple to configure, just setup it the normal way you do, and implement this pcc method, it will work. just make sure that you change the required data according to your network.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 16, 2013 @ 10:39 AM
Thank you for your reply, I asked you about setting up PPPoE server because I read your script in 4WAN PCC WITH PPPoE SERVER, I found you create a DHCP with PPPoE server and it’s not like the simple way, so it’s little bit confused me why you used DHCP with PPPoE Server?
about the DNS, do I enable allow remote for the DNS in PCC? what should I add to the configuration to speed up my browsing and http requests for the clients that connected to the PPPoE Server with PPPoE-Clients PCC routerboard?
These simple configuration like above, they are not simple like above, because they can make a very good advantage in your network, these configurations come with the experience. So, you have experience, and that why we like to follow your configuration step by step.
Thank you very much for everything you did and you will do, sharing your knowledge with everyone.
Thanks again Mr.Jahanzaib.
LikeLike
Comment by esalehnet — December 16, 2013 @ 11:51 AM
DHCP was configured because everything was on single RB, so providing IP to user was necessary for some local services like tv stream/fm, file sharing etc. for pppoe you usually dont need IP, but its good for monitoring/management purposes.
To increase HTTP response, you should add some good proxy server like SQUID cache to enhance the browsing experience with some extra caching of videos, and other dynamic contents and route the cached contents to user at full LAN speed using ZPH, this some times makes very dramatic effect to user browsing experience.
Also enable DNS in mikrotik and increase its cache size to some reasonable (according to the RB resources) as dns caching also plays slight impact by caching frequently accessed domains.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 16, 2013 @ 12:02 PM
Thanks for your reply.
So about the SQUID, how to create SQUID and ZPH for http caching without videos, and the recommended requirement PC for the SQUID?
I’m asking you that because here in Baghdad-IRAQ, we don’t have any specialist support for SQUID, is it easy to create and troubleshoot for me.
If you can provide me link or references for do that.
Thanks again.
LikeLike
Comment by esalehnet — December 16, 2013 @ 12:51 PM
Try this …
https://aacable.wordpress.com/tag/aacable-mikrotik-dstnat/
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 16, 2013 @ 12:58 PM
for this article https://aacable.wordpress.com/tag/aacable-mikrotik-dstnat/, can we use Mikrotik PCC instead of the DSL in the diagram?
LikeLike
Comment by esalehnet — December 16, 2013 @ 1:11 PM
yes you can,
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 17, 2013 @ 9:05 AM
i do have 2 DSL connections that give me the pppoe credentials. they do have different IPs and i would like to NAT on both of them for my LAN.
eth1 has ISP1 pppoe, eth2 has ISP2, eth3,4,5 has the LAN 192.168.6.0/24 and is doing NAT on both eth1,2 on equal basis. some help please, i am stuck with NAT. will i be able to access https with that?
LikeLike
Comment by john — December 28, 2013 @ 11:17 AM
please i do need some help to setup 2 different pppoes from 2 ISPs.
i do need it to loadbalanace the LAN
LikeLike
Comment by john — December 29, 2013 @ 9:04 PM
You can use this script to load balance multiple pppoe wan links , its doesn’t matter if they are from same ISP or different.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 30, 2013 @ 8:24 AM
Hello! Who can help me!? I need a script to configure 2 WAN Ports, and a PPPOE Server. Clients make a connection with PPPOE or a static IP address. WAN1 62.XX.XX.101/25, WAN2 62.XX.XX.125/25, PPPOE 10.10.10.1/24, The static IP address from the clients goes about the PPPOE Port or about a extra port? Sorry for my terrible english! Thanks for your help! santi.
LikeLike
Comment by santacruz65 — January 19, 2014 @ 5:49 PM
MR. Syed Jahanzaib Thank You For Evry Thing
i did with this script 4 line wan to export one line to lan
but cannot give me full speed for 4 lines please can you chek my configration or if you can make anew one for me
/interface ethernet
set 5 name=Local
set 1 name=WAN1
set 2 name=WAN2
set 3 name=WAN3
set 4 name=WAN4
/interface pppoe-client
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN1 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out1 password=hahaha \
profile=default service-name=”” use-peer-dns=no user=user-1
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN2 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out2 password=hahaha \
profile=default service-name=”” use-peer-dns=no user=user-2
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN3 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out3 password=hahaha \
profile=default service-name=”” use-peer-dns=no user=user-3
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN4 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out4 password=hahaha \
profile=default service-name=”” use-peer-dns=no user=user-4
/ip firewall mangle
add action=accept chain=prerouting disabled=no in-interface=pppoe-out1
add action=accept chain=prerouting disabled=no in-interface=pppoe-out2
add action=accept chain=prerouting disabled=no in-interface=pppoe-out3
add action=accept chain=prerouting disabled=no in-interface=pppoe-out4
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan1_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/0 src-address=172.16.0.0/16
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan2_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/1 src-address=172.16.0.0/16
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan3_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/2 src-address=172.16.0.0/16
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan4_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/3 src-address=172.16.0.0/16
add action=mark-routing chain=prerouting connection-mark=wan1_conn disabled=no new-routing-mark=to_wan1 passthrough=yes src-address=172.16.0.0/16
add action=mark-routing chain=prerouting connection-mark=wan2_conn disabled=no new-routing-mark=to_wan2 passthrough=yes src-address=172.16.0.0/16
add action=mark-routing chain=prerouting connection-mark=wan3_conn disabled=no new-routing-mark=to_wan3 passthrough=yes src-address=172.16.0.0/16
add action=mark-routing chain=prerouting connection-mark=wan4_conn disabled=no new-routing-mark=to_wan4 passthrough=yes src-address=172.16.0.0/16
/ip firewall nat
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out1 src-address=172.16.0.0/16
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out2 src-address=172.16.0.0/16
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out3 src-address=172.16.0.0/16
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out4 src-address=172.16.0.0/16
/ip route
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 routing-mark=to_wan1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 routing-mark=to_wan2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out3 routing-mark=to_wan3 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out4 routing-mark=to_wan4 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out3 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out4 scope=30 target-scope=10
/ip dns
set allow-remote-requests=no cache-max-ttl=1w cache-size=2048KiB \
max-udp-packet-size=4096 servers=8.8.8.8,8.8.4.4
LikeLike
Comment by ahmed al hanaty — January 25, 2014 @ 7:12 PM
What problem or error you are having?
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — January 28, 2014 @ 3:12 PM
when i make downlod the final was 2 lines if i disabeld 2 lines the same final disabled other the same final let 4 line also the same final i want to see in doenlod 1mb not 500 kb
LikeLike
Comment by ahmed al hanaty — January 31, 2014 @ 4:23 AM
Unable to understand your query. please refine your question.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — January 31, 2014 @ 9:02 AM
I try to put your configuration on my rb750 v 6.9. all marked routed will not reachable all route goes to route with scope=30 .. so strange .. any idea..
LikeLike
Comment by arif — February 1, 2014 @ 8:11 AM
i use this scribt to merge 4 line 2 m.b x 4 line = 8 m.b(1024k.b) in downlod but the final out put was 500 k.b in downlod
when used dhcp ip one line only
LikeLike
Comment by ahmed al hanaty — February 1, 2014 @ 3:14 PM
Its Work For Me..!! But I cannot open my modem interface @ 192.168.1.1 & 192.168.2.1
Can you give me the script?
Thanks..
LikeLike
Comment by Thomas — February 27, 2014 @ 5:24 AM
I want to open my modem to check adsl link quality & other setting.. Plz Help..
Thank You..
LikeLike
Comment by Thomas — February 27, 2014 @ 5:28 AM
You should exempt the modem ips from PCC. search google for this “howto exempt user from PCC”
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — February 27, 2014 @ 10:39 AM
mr ineed 4 wan pcc + fail over if you can help me
LikeLike
Comment by abdallah shehata — March 10, 2014 @ 3:08 PM
please
LikeLike
Comment by abdallah shehata — March 10, 2014 @ 3:08 PM
Hello
I really admire you and your work and i have been following your posts since i used mikrotik till now
this the first time i post a comment to you
i was just looking to your configuration and i have a question>
will it work for 100 pppoe as wan (from internet)
and ofcourse i have more than 400 pppoe users online?
regards
LikeLike
Comment by ali sam — March 14, 2014 @ 1:48 AM
Hello What if pppoe client not the same speed like pppoe client1 3.5mbps, pppoe client2 8mbps? What code should we change?
LikeLike
Comment by Lee Ratanak — April 1, 2014 @ 9:11 AM
you cant do much for this little difference.
also note that pcc is not very good with un equal wan links.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — April 1, 2014 @ 10:22 AM
hello bahie ya scrtip unequal wan link load balancing pa kam kray gie
LikeLike
Comment by shakaib — April 2, 2014 @ 6:27 PM
Hello and congratulations for the site,
I followed the guide but I have problems with the asterisk sip ..
how do I tell him that to reach 83.211.227.21 dall’isp1 always has to come out?
I’ve tried using “ip route rules” but then I have no problems with the return package ..
LikeLike
Comment by Frank — April 7, 2014 @ 11:35 PM
you have to exempt your SIP server ip from the pcc.
this way it will use only one way (whatever default route you set) for it.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — April 10, 2014 @ 9:46 AM
I want to open my modem to check adsl link quality & other setting.. Plz Help..
Thank You..
LikeLike
Comment by Salman — April 14, 2014 @ 3:37 PM
/ip firewall address-listadd list=exempt-from-pcc address=192.168.1.1/32
add list=exempt-from-pcc address=192.168.2.1/32
(change ips to your adsl modem ip’s)
/ip firewall mangleadd chain=prerouting dst-address-list=exempt-from-pcc action=accept
Move above mangle rule to TOP (above all other rules in mangle) .Try and let me know.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — April 14, 2014 @ 3:44 PM
No ……….sir not open ……..modem page
LikeLike
Comment by Salman — April 15, 2014 @ 7:15 AM
hmm perhaps something wrong with the config also.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — April 15, 2014 @ 8:37 AM
No …Sir….this rule is not working……..
LikeLike
Comment by Salman — April 15, 2014 @ 7:17 AM
Sir …………kya hum sey kuch mistake ho gai hai……?
configuration main.ya……..mangle rule main koi mistake hai……?
LikeLike
Comment by Salman — April 15, 2014 @ 9:42 PM
Sir …………did u tested that ip firewall rules….?
/ip firewall address-list
add list=exempt-from-pcc address=192.168.1.1/32
add list=exempt-from-pcc address=192.168.2.1/32
/ip firewall mangle
add chain=prerouting dst-address-list=exempt-from-pcc action=accept
Sir ……………its not working.
LikeLike
Comment by Salman — April 20, 2014 @ 6:27 AM
#You may try this script :
/ip firewall mangle
add chain=prerouting dst-address=192.168.1.1 action=mark-routing new-routing-mark=to-modem-1 passthrough=no
add chain=prerouting dst-address=192.168.2.1 action=mark-routing new-routing-mark=to-modem-2 passthrough=no
#move above mangle all other rules in mangle
/ip route
add gateway=192.168.1.1 routing-mark=to-modem-1
add gateway=192.168.2.1 routing-mark=to-modem-2
#let me know the result
LikeLike
Comment by Hidayat — April 24, 2014 @ 8:05 PM
Dear jahanzaib , which method i use , unequal wan link for load balancing ? (wan1 is 3 mb and wan2 is 5 mb ), because in your above post you say :”pcc is not very good with un equal wan links.” please advice ?
LikeLike
Comment by khurram — April 28, 2014 @ 8:59 AM
If I use one pppoe client and one wan? what i should changes?
LikeLike
Comment by Thomas — May 17, 2014 @ 1:17 AM
If I use one pppoe client and one dhcp wan? what i should changes? Thank you.
LikeLike
Comment by Thomas — May 17, 2014 @ 4:48 PM
hi how’re you?
Sorry if i’m bothering you but i’m trying to exclude an ip address from the load balancer and send it always to the second connection. Can you explain me where i’m wrong? This is my config:
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 \
routing-mark=to_WAN1 scope=30 target-scope=10
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 \
routing-mark=to_WAN2 scope=30 target-scope=10
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 scope=30 \
target-scope=10
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 scope=30 \
target-scope=10
add comment=“Default Route For Un-Marked Traffic” disabled=no distance=3 dst-address=0.0.0.0/0 gateway=pppoe-out2 scope=30 \
target-scope=10
/ip firewall mangle
add chain=prerouting comment=“Asterisk PBX” src-address=192.168.1.200
Thank you and best regards
LikeLike
Comment by Francesco Gabriele — June 5, 2014 @ 11:27 PM
I have applied These bellow code. But modem is still not opening. i checked the rule bytes and packets are counting in the rule but modem page is not working i have 2 Routerboard. 1 config as Hotspot. 2nd config as above loadblancing method.
Side Note:
If you are facing difficulty in opening dsl modem page, then try following code.
/ip firewall address-list
add list=exempt-from-pcc address=192.168.1.1/32
add list=exempt-from-pcc address=192.168.2.1/32
#(change ips to your adsl modem ip’s)
/ip firewall mangle
add chain=prerouting dst-address-list=exempt-from-pcc action=accept
Move above mangle rule to TOP (above all other rules in mangle) .Try and let me know.
LikeLike
Comment by Maria — June 17, 2014 @ 1:30 AM
javascript:HighlanderComments.cancelExternalWindow();
LikeLike
Comment by salman amin — June 20, 2014 @ 3:05 AM
hi dear zaib i run PCC and every thing is fine also i run it in a local network that has external users too wich connect to the router via vpn in local i have no problem but external users when connected to router i want use just one ADSL line how it is possible?
LikeLike
Comment by Mohammad Pf — September 10, 2014 @ 7:30 PM
Very good article. I’m trying to connect via L2TP but only one connection works at a time. I can connect through dialer1, if i disable dialer1 and reboot, i can connect only from dialer2 even if i enable dialer1 back, and so on
LikeLike
Comment by panosla1 — December 9, 2014 @ 12:16 AM
I bOught Mikrotik Rb750Gl But I Dont Know How To Configure Its Load Balance , Plz Tell Me If Any Body Knows.
LikeLike
Comment by Abdul Raheem — December 10, 2014 @ 9:07 AM
@Abdul Raheem
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — December 11, 2014 @ 3:01 PM
Syed Jahanzaib / Pinochio~:) R U There?
LikeLike
Comment by Abdul Raheem — December 10, 2014 @ 9:08 AM
I can download after apply this. But i can not browse the web pages. please reply
LikeLike
Comment by ronee — December 29, 2014 @ 9:47 AM
wouw mangle script amazing (y) (y) , thx mr. Syed Jahanzaib
LikeLike
Comment by Bambang H — January 8, 2015 @ 8:50 PM
syed jahanzaib ,,,,sir i need your help regarding mikrotik pppoe and hotspot server ,,,,,,can u help me,,,,????
LikeLike
Comment by zameer ahmed — February 5, 2015 @ 8:30 PM
@zameer, what help you required?
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — February 6, 2015 @ 8:12 AM
Hi, I would like to ask about port forwarding in a dual wan (PPPOE client) environment, but when I am using http://www.yougetsignal.com/tools/open-ports/ to check, ports sometimes close and sometimes open.
Could you please help me on this. Here is my network scenario:
Eth1: WAN 1 – A_PPPOE: Fixed IP address: 14.161.25.160
Eth2: WAN 2 – B_PPPOE: Dynamic IP address
Eth3: Guest LAN: 172.16.0.1/21
Eth4 bridge with Eth5, 6, 7: Local LAN: 192.168.1.1/24
I would like to open the following ports:
1) 8080 on 192.168.1.50 (NAS)
2) 100, 37779 on 192.168.1.2 (Remote CCTV)
Here is my config:
/ip firewall mangle
add action=accept chain=prerouting disabled=no in-interface=A_PPPOE
add action=accept chain=prerouting disabled=no in-interface=B_PPPOE
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan1_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:2/0 src-address=192.168.1.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan2_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:2/1 src-address=192.168.1.0/24
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan1_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:2/0 src-address=172.16.0.0/21
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan2_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:2/1 src-address=172.16.0.0/21
add action=mark-routing chain=prerouting connection-mark=wan1_conn disabled=no new-routing-mark=to_wan1 passthrough=yes src-address=192.168.1.0/24
add action=mark-routing chain=prerouting connection-mark=wan2_conn disabled=no new-routing-mark=to_wan2 passthrough=yes src-address=192.168.1.0/24
add action=mark-routing chain=prerouting connection-mark=wan1_conn disabled=no new-routing-mark=to_wan1 passthrough=yes src-address=172.16.0.0/21
add action=mark-routing chain=prerouting connection-mark=wan2_conn disabled=no new-routing-mark=to_wan2 passthrough=yes src-address=172.16.0.0/21
/ip firewall nat
add action=masquerade chain=srcnat disabled=no out-interface=A-PPPOE src-address=172.16.0.0/20
add action=masquerade chain=srcnat disabled=no out-interface=B-PPPOE src-address=172.16.0.0/20
add action=masquerade chain=srcnat disabled=no out-interface=A-PPPOE src-address=172.16.0.0/22
add action=masquerade chain=srcnat disabled=no out-interface=B-PPPOE src-address=172.16.0.0/22
/ip route
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=A_PPPOE routing-mark=to_wan1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=B_PPPOE routing-mark=to_wan2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=A_PPPOE scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=B_PPPOE scope=30 target-scope=10
/ip firewall nat
add action=dst-nat chain=dstnat disabled=no dst-address-type=local dst-port=8080 in-interface=all-ppp protocol=tcp to-addresses=192.168.1.50 to-ports=8080
add action=dst-nat chain=dstnat disabled=no dst-address-type=local dst-port=100 in-interface=all-ppp protocol=tcp to-addresses=192.168.1.2 to-ports=100
add action=dst-nat chain=dstnat disabled=no dst-address-type=local dst-port=37779 in-interface=all-ppp protocol=tcp to-addresses=192.168.1.2 to-ports=37779
Btw, I am using the below script to update my IP in Dyndns and it works fine.
# Set needed variables
:local username “abc”
:local password “zyx”
:local hostname “hotel123.homeip.net”
:global dyndnsForce
:global previousIP
# print some debug info
:log info (“UpdateDynDNS: username = $username”)
:log info (“UpdateDynDNS: password = $password”)
:log info (“UpdateDynDNS: hostname = $hostname”)
:log info (“UpdateDynDNS: previousIP = $previousIP”)
# get the current IP address from the internet (in case of double-nat)
/tool fetch mode=http address=”checkip.dyndns.org” src-path=”/” dst-path=”/dyndns.checkip.html”
:delay 1
:local result [/file get dyndns.checkip.html contents]
# parse the current IP result
:local resultLen [:len $result]
:local startLoc [:find $result “: ” -1]
:set startLoc ($startLoc + 2)
:local endLoc [:find $result “” -1]
:local currentIP [:pick $result $startLoc $endLoc]
:log info “UpdateDynDNS: currentIP = $currentIP”
# Remove the # on next line to force an update every single time – useful for debugging,
# but you could end up getting blacklisted by DynDNS!
#:set dyndnsForce true
# Determine if dyndns update is needed
# more dyndns updater request details http://www.dyndns.com/developers/specs/syntax.html
:if (($currentIP != $previousIP) || ($dyndnsForce = true)) do={
:set dyndnsForce false
:set previousIP $currentIP
:log info “$currentIP or $previousIP”
/tool fetch user=$username password=$password mode=http address=”members.dyndns.org” \
src-path=”nic/update?system=dyndns&hostname=$hostname&myip=$currentIP&wildcard=no” \
dst-path=”/dyndns.txt”
:delay 1
:local result [/file get dyndns.txt contents]
:log info (“UpdateDynDNS: Dyndns update needed”)
:log info (“UpdateDynDNS: Dyndns Update Result: “.$result)
:put (“Dyndns Update Result: “.$result)
} else={
:log info (“UpdateDynDNS: No dyndns update needed”)
}
LikeLike
Comment by Lee Zen — February 17, 2015 @ 12:52 PM
really nice tutorial. i have failed to make it work in my case !
i do have a mikrotik 750 with 2 adsl connections that i would like to get my LAN to load balance over them. could someone send me his/her backup please?
LikeLike
Comment by john — June 14, 2015 @ 8:47 PM
Dear all. i am having a trouble to create my config and i would like some help over that. i do have 2 vdsl connections and i do need to create load balance/failover without having issues in ftp, https.
i do need eth1 & 2 to have the wan1 & 2 respectively.
-wan1:has the modem in bridge mode and has the IP 192.168.1.1
-wan2:has the modem in bridge mode and has the IP 192.168.2.1
-eth3:has the subnet 192.168.3.0/24 access the LAN at full speed but the internet at 10/1M. cannot see any other subnet, apart from its own
-eth4:has the subnet 192.168.4.0/24. access the LAN at full speed but the internet at 20/3M. cannot see any other subnet apart from 192.168.5.0/24 and its own,
-eth5:has the subnet 192.168.5.0/24.access the LAN at full speed but the internet at 70/6M. cannot see any other subnet apart from 192.168.4.0/24 and its own,
-port forward for both WANs for port 22, 443 TCP at 192.168.3.100
could someone help me with the script please?
LikeLike
Comment by atux atux — June 18, 2015 @ 11:24 AM
very nice
LikeLike
Comment by DANIAL KAZEMI — July 29, 2015 @ 10:05 AM
AOA JAHANZAIB BHAI i have one question,
does client internet will work without configuring Pppoe Setup on his pc.
i am using this
/ip address
add address=192.168.50.2/24 network=192.168.50.0 broadcast=192.168.50.255 interface=Local
add address=192.168.1.2/24 network=192.168.1.0 broadcast=192.168.1.255 interface=WAN1
add address=192.168.2.2/24 network=192.168.2.0 broadcast=192.168.2.255 interface=WAN2
/ip firewall mangle
add chain=input in-interface=WAN1 action=mark-connection new-connection-mark=WAN1_conn
add chain=input in-interface=WAN2 action=mark-connection new-connection-mark=WAN2_conn
add chain=output connection-mark=WAN1_conn action=mark-routing new-routing-mark=to_WAN1
add chain=output connection-mark=WAN2_conn action=mark-routing new-routing-mark=to_WAN2
add chain=prerouting dst-address=192.168.1.0/24 action=accept in-interface=Local
add chain=prerouting dst-address=192.168.2.0/24 action=accept in-interface=Local
add chain=prerouting dst-address-type=!local in-interface=Local per-connection-classifier=both-addresses-and-ports:3/0 action=mark-connection new-connection-mark=WAN1_conn passthrough=yes
add chain=prerouting dst-address-type=!local in-interface=Local per-connection-classifier=both-addresses-and-ports:3/1 action=mark-connection new-connection-mark=WAN2_conn passthrough=yes
add chain=prerouting connection-mark=WAN1_conn in-interface=Local action=mark-routing new-routing-mark=to_WAN1
add chain=prerouting connection-mark=WAN2_conn in-interface=Local action=mark-routing new-routing-mark=to_WAN2
/ip route
add dst-address=0.0.0.0/0 gateway=192.168.1.1 routing-mark=to_WAN1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.2.1 routing-mark=to_WAN2 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.1.1 distance=1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.2.1 distance=2 check-gateway=ping
/ip firewall nat
add chain=srcnat out-interface=WAN1 action=masquerade
add chain=srcnat out-interface=WAN2 action=masquerade
/ppp profile
set 0 change-tcp-mss=yes name=default only-one=default use-compression=default use-encryption=default use-mpls=default use-vj-compression=default
add change-tcp-mss=default dns-server=192.168.50.1 local-address=pool1 name=”1MB pro” only-one=yes rate-limit=256k/1024k use-compression=default \
use-encryption=default use-mpls=default use-vj-compression=default
set 2 change-tcp-mss=yes name=default-encryption only-one=default use-compression=default use-encryption=yes use-mpls=default use-vj-compression=default
/ppp aaa
set accounting=yes interim-update=0s use-radius=no
/ppp secret
add caller-id=”” disabled=no limit-bytes-in=0 limit-bytes-out=0 local-address=192.168.50.2 name=user-1 password=user profile=”1MB pro” remote-address=\
192.168.50.51 routes=”” service=pppoe
help me if i am wrong some where .. Client internet is working without any pppoe setup.. internet will work at client pc on simple lan setting :O
Thanks
LikeLike
Comment by Bangash — August 8, 2015 @ 12:35 AM
by default if your NAT rule allows * ALL ips in src address, internet will work at user end even without connecting pppoe dialer.
make sureyou allow only pppoe client ips (which must be differetn subent ip series then you rlocal lan) in src address of default nat rules.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — August 8, 2015 @ 7:54 PM
Sir………..whatsapp videos slow and no downloading on loadbalancer pcc method
if i connected direct vdsl modem via wifi than perfect download the videos from whatsapp
how can i solved this problem…………?
ALLAH aap ko jaza e khair dey
LikeLike
Comment by Salman — January 3, 2016 @ 7:07 PM
Hi. I have a MiktoTik RB951Ui-2Hnd and 3 WAN, 1 LAN. I am configed this with FailOver and LoadBalance. Now I have a problem with FTP, HTTPS. How do I to do, that work my FTP, HTTPS good without IP changing. Thanks.
LikeLike
Comment by Max_Cohen — March 24, 2016 @ 2:55 PM
use src-address base load balancing, and most of problems will auto solve. read about src-address.\
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — March 26, 2016 @ 4:58 PM
I have used this configuration on RB951G-2HND for 2 x ptcl lines with 8Mb each but it’s not load balancing. Only one link works at a time. If I disable one the load shifts to the other but the 2 lines are never combined. Can you please help? Also, can you confirm if this script you gave works for failover scenario automatically?
LikeLike
Comment by Faizan — March 28, 2016 @ 9:29 PM
Is this script running in hotspot mode? We want to run it in this hotspot. Waiting for your assistance , I offer best regards
LikeLike
Comment by İsmail Yıldırım — March 30, 2016 @ 9:44 PM
I have 1 pppoe (physical) and 1 pppoe (VLAN). I’ve done the steps above, but only pppoe (physical) activity, while pppoe (VLAN) is inactive. I want both operations. Please help me how to fix it.
—————————-
Ether 1 : Lan
Ether 2 : Wan1
Vlan-Wan1
Ether 3 : Wan2
PPPoe1 : Interface : Vlan-Wan1
PPPoe2 : Interface : Wan2
—————————–
/ip address
add address=11.10.84.1/24 network=11.10.84.0 broadcast=11.10.84.255 interface=Local
add address=19.85.1.2/24 network=19.85.1.0 broadcast=19.85.1.255 interface=Vlan-Wan1
add address=19.85.2.2/24 network=19.85.2.0 broadcast=19.85.2.255 interface=Wan2
/ip firewall mangle
add chain=input in-interface=Vlan-Wan1 action=mark-connection new-connection-mark=Wan1_conn
add chain=input in-interface=Wan2 action=mark-connection new-connection-mark=Wan2_conn
add chain=output connection-mark=Wan1_conn action=mark-routing new-routing-mark=to_Wan1
add chain=output connection-mark=Wan2_conn action=mark-routing new-routing-mark=to_Wan2
add chain=prerouting dst-address=19.85.1.0/24 action=accept in-interface=Local
add chain=prerouting dst-address=19.85.2.0/24 action=accept in-interface=Local
add chain=prerouting dst-address-type=!local in-interface=Local per-connection-classifier=both-addresses-and-ports:2/0 action=mark-connection new-connection-mark=Wan1_conn passthrough=yes
add chain=prerouting dst-address-type=!local in-interface=Local per-connection-classifier=both-addresses-and-ports:2/1 action=mark-connection new-connection-mark=Wan2_conn passthrough=yes
add chain=prerouting connection-mark=Wan1_conn in-interface=Local action=mark-routing new-routing-mark=to_Wan1
add chain=prerouting connection-mark=Wan2_conn in-interface=Local action=mark-routing new-routing-mark=to_Wan2
/ip route
add dst-address=0.0.0.0/0 gateway=19.85.1.1 routing-mark=to_Wan1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=19.85.2.1 routing-mark=to_Wan2 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=19.85.1.1 distance=1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=19.85.2.1 distance=2 check-gateway=ping
/ip firewall nat
nat add chain=srcnat out-interface=Vlan-Wan1 action=masquerade
nat add chain=srcnat out-interface=Wan2 action=masquerade
nat add action=accept chain=pre-hotspot disabled=no dst-address-type=!local hotspot=auth
LikeLike
Comment by huyhoangcao — April 21, 2016 @ 7:25 PM
Hello I have a router Board in 2011 enabled as possible to speed up YouTube and Facebook with many thanks
LikeLike
Comment by soso197080 — April 22, 2016 @ 4:32 PM
Hi Sayed, i have Mikrotik rb750 router and the one static ip in WAN 1 and second port configured PPOE , we set up both are load balancing but we facing some site is not load properly and some site not working..pls suggest.
192.168.5.1/24 – Lan 1
203.88.139.122/30 – wan1
203.88.139.122/30 – WAN2
LikeLike
Comment by ronak shah — April 29, 2016 @ 5:28 PM
Hi Syed, I have Microtik CRS 125-24G-1S-2HnD. I have configured 2 static IP and 1 PPPoE. I Don’t want the load balancing, so i created IP based routing. i.e 192.168.0.110 – 120 will go via routing-mark=ARG. I have appended list of IP in address list name=AR and created a mangle rule with prerouting the source address list (AR). This works.
I am looking for a failover. I tried the below configuration. but upon loading the below configuration, the PPPoE doesn’t work. any idea ?
#122.166.234.70 begaluru DNS
#115.112.236.5 hyderbad DNS
#115.248.164.237 mumbai DNS
#14.102.53.148 newdelhi DNS
/ip route
add dst-address=122.166.234.70 gateway=192.168.2.1 scope=10
add dst-address=115.112.236.5 gateway=192.168.2.1 scope=10
add dst-address=122.166.234.70 gateway=192.168.1.1 scope=10
add dst-address=115.112.236.5 gateway=192.168.1.1 scope=10
add dst-address=115.248.164.237 gateway=pppoe-WAN3 scope=10
add dst-address=14.102.53.148 gateway=pppoe-WAN3 scope=10
#Then, let’s create destinations to “virtual” hops to use in further routes. I’m using 10.1.1.1 and 10.2.2.2 as an example:
/ip route
add dst-address=10.1.1.1 gateway=122.166.234.70 scope=10 target-scope=10 check-gateway=ping comment=”Virtual host for ISP1-host1″
add dst-address=10.1.1.1 gateway=115.112.236.5 scope=10 target-scope=10 check-gateway=ping comment=”Virtual host for ISP1-host2″
add dst-address=10.2.2.2 gateway=122.166.234.70 scope=10 target-scope=10 check-gateway=ping comment=”Virtual host for ISP2-host1″
add dst-address=10.2.2.2 gateway=115.112.236.5 scope=10 target-scope=10 check-gateway=ping comment=”Virtual host for ISP2-host2″
add dst-address=10.3.3.3 gateway=115.248.164.237 scope=10 target-scope=10 check-gateway=ping comment=”Virtual host for ISP3-host1″
add dst-address=10.3.3.3 gateway=14.102.53.148 scope=10 target-scope=10 check-gateway=ping comment=”Virtual host for ISP3-host2″
And now we may add default routes for clients:
/ip route
add distance=1 gateway=10.1.1.1
add distance=1 gateway=10.2.2.2
add distance=1 gateway=10.3.3.3 routing-mark=ARG
add distance=2 gateway=10.1.1.1 routing-mark=ARG
add distance=2 gateway=10.2.2.2 routing-mark=ARG
add distance=2 gateway=10.3.3.3
LikeLike
Comment by John Britto — June 13, 2016 @ 12:24 PM
its better if you make script to do the fail over , because with script you can get much customized results.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — June 15, 2016 @ 10:21 AM
hi i am a big fan of ur work and mostly i find solutions to the hard situations in this marvelous blog
so i am in such hard time and i really need ur help sir
i have a 1mb pppoe username and my dsl line is a 8 mb line
so i needed to multiple the user in the pppoe-out interfaces and this did go well for some fine time
8 pppoe-out on the same lan card and we have 8mbs of speed which is our goal
but now the isp blocked this and every mac address is limited for 1 ip addressee so the pppoe-out1 would get ip but none of the others
some friend suggested that we can use the vrrp putting the vrrp over the lan and putting the ppoe-out over the vrrp but it didn’t get any connections not even the 1 connection that the normal way gave when i put the pppoe directly on the lan card
so i needed many nics to solve this i used vmware cuz it gives 10 nic adapters
now i have 1 lan card as local and 8 cards as wan1-wan8 and an extra spare card
the idea theoretically gone well now i have 8 pppoe-out over 8 virtual lan cards those are bridged over 1 real lan card in my pc
and all of the 8 gets ips from the isp but the problem is that the mikrotik wont add up the speeds of them it only gives my the speed of 1 of them randomly every time i try to connect after trying the pcc way and i tried some other ways like nth and it didn’t give me any internet just ping replies fine but no traffic
can u please help me get internet from the 8 ips i am having from the isp
i tried the scripts in this post put i didn’t get nigher ping replies nor internet traffic nothing at all
i really need ur help so much
thank u
and sorry for my bad english
LikeLike
Comment by ehab — June 17, 2016 @ 11:26 PM
I’m facing a huge problem in a case with a 4 WAN load balancing scenario. At the beggining ther was load balancing but afte a week or so hell broke loose. The scripting is the following:
/ip firewall mangle
add action=accept chain=prerouting dst-address=192.168.0.0/24
add action=mark-connection chain=prerouting connection-mark=no-mark disabled=no dst-address-type=!local in-interface=ether6-lan-master new-connection-mark=WAN1_conn passthrough=yes per-connection-classifier=src-address:4/0
add action=mark-connection chain=prerouting connection-mark=no-mark disabled=no dst-address-type=!local in-interface=ether6-lan-master new-connection-mark=WAN2_conn passthrough=yes per-connection-classifier=src-address:4/1
add action=mark-connection chain=prerouting connection-mark=no-mark disabled=no dst-address-type=!local in-interface=ether6-lan-master new-connection-mark=WAN3_conn passthrough=yes per-connection-classifier=src-address:4/2
add action=mark-connection chain=prerouting connection-mark=no-mark disabled=no dst-address-type=!local in-interface=ether6-lan-master new-connection-mark=WAN4_conn passthrough=yes per-connection-classifier=src-address:4/3
add action=mark-routing chain=prerouting connection-mark=WAN1_conn disabled=no in-interface=ether6-lan-master new-routing-mark=to_WAN1 passthrough=yes
add action=mark-routing chain=prerouting connection-mark=WAN2_conn disabled=no in-interface=ether6-lan-master new-routing-mark=to_WAN2 passthrough=yes
add action=mark-routing chain=prerouting connection-mark=WAN3_conn disabled=no in-interface=ether6-lan-master new-routing-mark=to_WAN3 passthrough=yes
add action=mark-routing chain=prerouting connection-mark=WAN4_conn disabled=no in-interface=ether6-lan-master new-routing-mark=to_WAN4 passthrough=yes
add action=mark-routing chain=output connection-mark=WAN1_conn disabled=no new-routing-mark=to_WAN1 passthrough=yes
add action=mark-routing chain=output connection-mark=WAN2_conn disabled=no new-routing-mark=to_WAN2 passthrough=yes
add action=mark-routing chain=output connection-mark=WAN3_conn disabled=no new-routing-mark=to_WAN3 passthrough=yes
add action=mark-routing chain=output connection-mark=WAN4_conn disabled=no new-routing-mark=to_WAN4 passthrough=yes
add action=mark-connection chain=prerouting connection-mark=no-mark disabled=no in-interface=Otenet1 new-connection-mark=WAN1_conn passthrough=yes
add action=mark-connection chain=prerouting connection-mark=no-mark disabled=no in-interface=Otenet2 new-connection-mark=WAN2_conn passthrough=yes
add action=mark-connection chain=prerouting connection-mark=no-mark disabled=no in-interface=Otenet3 new-connection-mark=WAN3_conn passthrough=yes
add action=mark-connection chain=prerouting connection-mark=no-mark disabled=no in-interface=Otenet4 new-connection-mark=WAN4_conn passthrough=yes
/ip firewall nat
add action=masquerade chain=srcnat out-interface=Otenet1 src-address=192.168.0.0/24
add action=masquerade chain=srcnat out-interface=Otenet2 src-address=192.168.0.0/24
add action=masquerade chain=srcnat out-interface=Otenet3 src-address=192.168.0.0/24
add action=masquerade chain=srcnat out-interface=Otenet4 src-address=192.168.0.0/24
/ip route
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=Otenet1 routing-mark=to_WAN1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=Otenet2 routing-mark=to_WAN2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=Otenet3 routing-mark=to_WAN3 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=Otenet4 routing-mark=to_WAN4 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=Otenet1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=Otenet2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=3 dst-address=0.0.0.0/0 gateway=Otenet3 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=4 dst-address=0.0.0.0/0 gateway=Otenet4 scope=30 target-scope=10
/ip firewall filter
add action=drop chain=input comment=”Drop Invalid connections” connection-state=invalid in-interface=Otenet1
add action=drop chain=input comment=”Drop Invalid connections” connection-state=invalid in-interface=Otenet2
add action=drop chain=input comment=”Drop Invalid connections” connection-state=invalid in-interface=Otenet3
add action=drop chain=input comment=”Drop Invalid connections” connection-state=invalid in-interface=Otenet4
add chain=input comment=”Allow Established connections” connection-state=established in-interface=Otenet1
add chain=input comment=”Allow Established connections” connection-state=established in-interface=Otenet2
add chain=input comment=”Allow Established connections” connection-state=established in-interface=Otenet3
add chain=input comment=”Allow Established connections” connection-state=established in-interface=Otenet4
add chain=input comment=”Allow Related connections” connection-state=related in-interface=Otenet1
add chain=input comment=”Allow Related connections” connection-state=related in-interface=Otenet2
add chain=input comment=”Allow Related connections” connection-state=related in-interface=Otenet3
add chain=input comment=”Allow Related connections” connection-state=related in-interface=Otenet4
add chain=input comment=”Allow ICMP” in-interface=Otenet1 protocol=icmp
add chain=input comment=”Allow ICMP” in-interface=Otenet2 protocol=icmp
add chain=input comment=”Allow ICMP” in-interface=Otenet3 protocol=icmp
add chain=input comment=”Allow ICMP” in-interface=Otenet4 protocol=icmp
add chain=input comment=”Allow winbox, pptp” connection-state=new dst-port=8291,1723 in-interface=Otenet1 protocol=tcp
add chain=input comment=”Allow winbox, pptp” connection-state=new dst-port=8291,1723 in-interface=Otenet2 protocol=tcp
add chain=input comment=”Allow winbox, pptp” connection-state=new dst-port=8291,1723 in-interface=Otenet3 protocol=tcp
add chain=input comment=”Allow winbox, pptp” connection-state=new dst-port=8291,1723 in-interface=Otenet4 protocol=tcp
add action=drop chain=input disabled=yes dst-port=53 in-interface=Otenet1 protocol=udp
add action=drop chain=input disabled=yes dst-port=53 in-interface=Otenet2 protocol=udp
add action=drop chain=input disabled=yes dst-port=53 in-interface=Otenet3 protocol=udp
add action=drop chain=input disabled=yes dst-port=53 in-interface=Otenet4 protocol=udp
add action=drop chain=input comment=”Drop everything else” in-interface=Otenet1
add action=drop chain=input comment=”Drop everything else” in-interface=Otenet2
add action=drop chain=input comment=”Drop everything else” in-interface=Otenet3
add action=drop chain=input comment=”Drop everything else” in-interface=Otenet4
add action=drop chain=forward comment=”Drop Invalid connections” connection-state=invalid in-interface=Otenet1 protocol=tcp
add action=drop chain=forward comment=”Drop Invalid connections” connection-state=invalid in-interface=Otenet2 protocol=tcp
add action=drop chain=forward comment=”Drop Invalid connections” connection-state=invalid in-interface=Otenet3 protocol=tcp
add action=drop chain=forward comment=”Drop Invalid connections” connection-state=invalid in-interface=Otenet4 protocol=tcp
add chain=forward comment=”Allow Established connections” connection-state=established in-interface=Otenet1
add chain=forward comment=”Allow Established connections” connection-state=established in-interface=Otenet2
add chain=forward comment=”Allow Established connections” connection-state=established in-interface=Otenet3
add chain=forward comment=”Allow Established connections” connection-state=established in-interface=Otenet4
add chain=forward comment=”Allow Related connections” connection-state=related in-interface=Otenet1
add chain=forward comment=”Allow Related connections” connection-state=related in-interface=Otenet2
add chain=forward comment=”Allow Related connections” connection-state=related in-interface=Otenet3
add chain=forward comment=”Allow Related connections” connection-state=related in-interface=Otenet4
I run this on a mikrotik 3011.
Any ideas where is the mistake?
Thank in advace even for looking at it.
LikeLike
Comment by Spyros — July 21, 2016 @ 9:59 AM
Hi I have used your PCC load balance and it is working fine on my one Lan (ether 5)
my setup is as follow
Ether 1 -> PPPoe server
Ether 2 -> ADSL Modem 1
Ether 3 -> ADSL Modem 2
Ether 5 -> RB 2 in network with own PPPOE server
WAN1 -> ADSL 1 PPPOE
WAN2 -> ADSL 2 PPPOE
How do i Load balnce both Ether 1 and 5
Thanks
Jan
LikeLike
Comment by Jan — August 26, 2016 @ 2:21 PM
2 PPPOE DHCP WAN
1 WLAN DHCP WAN
1 LAN 192.168.88.1 LOAD BALANCING & PCC
CONFIGRATION PLZ SEND
LikeLike
Comment by Abdul — November 19, 2016 @ 6:31 PM
Hi Syed,
My setup is 4-WANS.
I have 3 Adsl WAN lines and 1 Static Ip from another ISP.
Can you assist with the script?
LikeLike
Comment by Felix — May 29, 2017 @ 2:55 PM
[…] https://aacable.wordpress.com/2013/12/06/mikrotik-dual-wan-pppoe-client-pcc-with-pppoe-server/ […]
LikeLike
Pingback by Mikrotik Dual WAN [pppoe-client] PCC with PPPoE Server | emek — June 14, 2017 @ 4:23 PM
Dear sir. Really nice post. I tried to follow it and i ended up with errors. my setup has a RB750, 2 dsl connections in bridge mode. the first ISP has credentials usera@ispa.com with password x1234. The second ISP has xyzuser@abcde.com with password abxyz. LAN is 192.168.178.0/24. eth1-3 is my LAN. eth4 ISPA, eth5 ISPB. I have done it so wrong and i cannot use it now. Some help please?
LikeLike
Comment by john — July 18, 2017 @ 12:10 PM
sir bhai mara pass 2 router hai load balancing kasa kara our hotspot dosra ma kasa kara is ka koi script hai?
LikeLike
Comment by khudadad baloch — July 29, 2017 @ 1:25 AM
sir i have a problem on my load balancing, when i didnt bridged mode the 2 WANS, it has no problem but in bridged mode (pppoe client) it stops load balancing, fyi, my 2 WAN are now in bridge mode and they have the same gateway because they are the same ISP. hope for your fast reply
LikeLike
Comment by ASterisk — August 8, 2017 @ 7:24 AM
hello bro i have 8 WAN link pppoe-out
my problem the link speed are unequal examp : wan1 wan2 wan3 wan4 wan5 wan6 3MB
and wan7 wan8 10MB
what i have to do ?
the output bandwidth is wrong the WAN7 WAN8 Wont work correctly with the other wan link
there is any idea how to fix that?
or there is any other method than load balancing ?
thank you
LikeLike
Comment by ELie — August 31, 2017 @ 7:03 PM
In my Mikrotik (rb750r2 ) router I have setup hotspot. I am having an ILL with static IP as mainline and another DSL line as back up.
Every time my ILL goes down I have to manually put the DSL cable and reconfigure the dhcp client in my Mikrotik router.
I really need help to setup failover on the same router. I have gone through lots of articles but all are PCC load balancing which I dont want.
Please publish an article which will do failover with hotspot on the same router.
LikeLike
Comment by Anupam Pradhan — November 6, 2017 @ 11:39 AM
Thank you for the script! I have 2 wan pppoe. From one internet wan 1 i am behind the nat (i get private ip) and wan 2 got directly connected and get public ip. Wan 1 is unlimited internet but can not run website on it due to the private ip provided by the isp. I used your script and also add port forwarding feature in the mickrotik. Now my website works from public ip from wan 2 and the traffic is diverted through wan 1 which is unlimited internet . Its like users are entering one gate and leaving from another.
THanks again
LikeLike
Comment by Neeraj Kakar — December 25, 2017 @ 2:08 PM
Sir I have a assignment to make 2 pppoe client which easily added but main work is that to dial one pppoe1 by default if pppoe1 did not connect in 5 mint dial then dial pppoe2 and when pppoe1 is back dial pppoe1 can i get any help about that.?
LikeLike
Comment by Tahseen Ahmad — April 22, 2018 @ 1:02 PM
you can simple schedule a script that should run after every 5 minutes. It should pppoe-out1 status , if it’s not connected then simply enable-pppoe-out1 dialer ,
and on next run if pppoe-out status is connected then disable the pppoe-out2.
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — April 25, 2018 @ 8:15 AM
thanks
LikeLike
Comment by Tahseen Ahmad — April 25, 2018 @ 10:39 AM
one think i tell you good scrift for load balence
LikeLike
Comment by satish — July 28, 2018 @ 12:09 PM
this is satish from SKE CityOnlines Services Pvt Ltd
Load Balence with 2 deferent Pppoe 1 lan out put without isuues https and fttp Its work
/interface pppoe-client
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN1 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out1 password=hahaha \
profile=default service-name=”” use-peer-dns=no user=user-1
add ac-name=”” add-default-route=no allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=yes interface=WAN2 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out2 password=hahaha \
profile=default service-name=”” use-peer-dns=no user=user-2
### Starting the MANGLE MAGIC : ) PCC SCRIPTING START Here (Satish)
/ip firewall mangle
add action=accept chain=prerouting disabled=no in-interface=pppoe-out1
add action=accept chain=prerouting disabled=no in-interface=pppoe-out2
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan1_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:2/0 src-address=172.16.0.0/16
add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan2_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:2/1 src-address=172.16.0.0/16
add action=mark-routing chain=prerouting connection-mark=wan1_conn disabled=no new-routing-mark=to_wan1 passthrough=yes src-address=172.16.0.0/16
add action=mark-routing chain=prerouting connection-mark=wan2_conn disabled=no new-routing-mark=to_wan2 passthrough=yes src-address=172.16.0.0/16
### NATTING both WAN connection for PPPoE IP Pool users only
/ip firewall nat
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out1 src-address=172.16.0.0/16
add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out2 src-address=172.16.0.0/16
### Setting Default Routes for MARKED packets for both WAN and for local router use. (satish)
/ip route
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 routing-mark=to_wan1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 routing-mark=to_wan2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 scope=30 target-scope=10
IF you not able to acces from out side your router pages plz add that adress in ip-firewall- adress list add that ips
/ip firewall mangle
add chain=prerouting dst-address-list=exempt-from-pcc action=accept
Attenction: Dont forget about Pppoe logs
LikeLike
Comment by satish — July 28, 2018 @ 12:16 PM
trying to setup dual wan load balancing in my Mikrotik. I have two 50M from same ISP and it provides pppoe. Always uses only 1 connection, never the 2nd, even if i disconnect the cable from 1st pppoe.
Here is my config
Code: Select all
/interface bridge
add name=LAN
/interface wireless
set [ find default-name=wlan1 ] ssid=MikroTik
/interface ethernet
set [ find default-name=ether1 ] name=WAN1
set [ find default-name=ether2 ] name=WAN2
/interface pppoe-client
add add-default-route=yes disabled=no interface=WAN1 name=pppoe-WAN1 \
password=mn57zf2 use-peer-dns=yes user=atux@otenet.gr
add add-default-route=yes disabled=no interface=WAN2 name=pppoe-WAN2 \
password=98%xvzf use-peer-dns=yes user=null@otenet.gr
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp_pool0 ranges=192.168.88.200-192.168.88.254
/ip dhcp-server
add address-pool=dhcp_pool0 disabled=no interface=LAN name=dhcp1
/tool user-manager customer
set admin access=\
own-routers,own-users,own-profiles,own-limits,config-payment-gw
/interface bridge port
add bridge=LAN interface=ether3
add bridge=LAN interface=wlan1
/ip address
add address=192.168.88.1/24 interface=LAN network=192.168.88.0
/ip cloud
set update-time=no
/ip dhcp-server network
add address=192.168.88.0/24 dns-server=192.168.88.1 gateway=192.168.88.1
/ip dns
set allow-remote-requests=yes servers=8.8.8.8,8.8.4.4
/ip firewall nat
# pppoe-WAN1 ready
add action=masquerade chain=srcnat out-interface=pppoe-WAN1
# pppoe-WAN2 ready
add action=masquerade chain=srcnat out-interface=pppoe-WAN2
/tool user-manager database
set db-path=user-manager
I am trying to achieve a better utilization of both xDSL lines and in case of multiple connections to use both. So if a user opens many sessions in a browser, then it will use both pppoes.
could you help me please, to correct my config?
LikeLike
Comment by john — October 3, 2019 @ 10:18 AM
How to Dial Multiple PPPOE Client Over Single WAN Interface in Mikrotik. And load their balance.
Dial ppooe 1,2,3 so on in one interface Wan and
Out their loadbalance in one port Lan
LikeLike
Comment by Yasir — April 4, 2020 @ 10:04 AM