Following post is an reference guide or scrapbook, which have working codes for following.
- Dual WAN PCC with 2 DSL modems [configured in bridge mode] and dialing is done via mikrotik
- Port forwarding various ports [as required] from the internet to local web server
- PPPoE Server
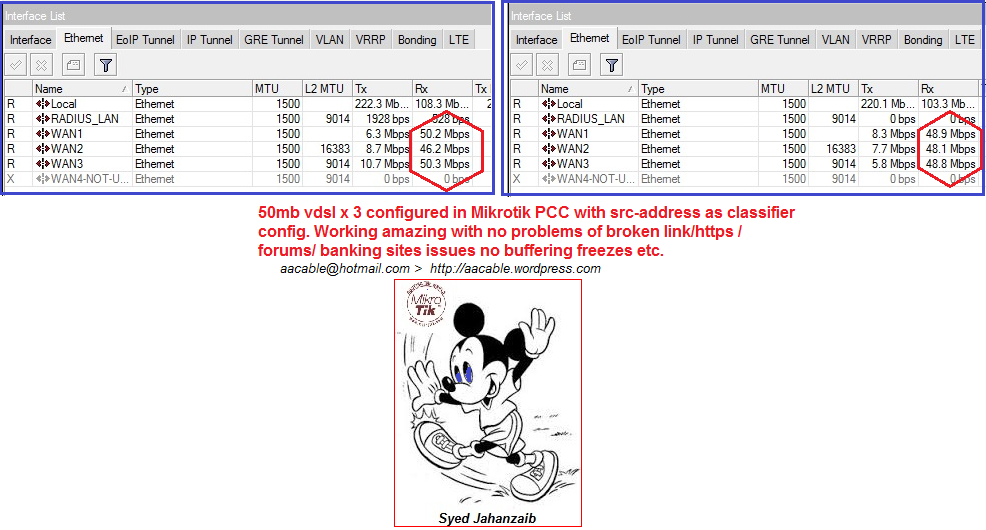
Note: I have used SOURCE BASE classifier in this example, to avoid common load balancing problems like https links breakup, buffering issues stuck problem etc etc : )
Just to remind this is not a copy paste version. its not complete export version. I modified the data for reference. Read them carefully for better understanding. You can pick any section of your choice or as required. I will add more sections later …
NETWORK DETAiLS :
Mikrotik LAN Interface name = Local
Mikrotik WAN 1 interface name = WAN1
Mikrotik WAN 2 interface name = WAN2
Mikrotik LAN IP Address = 192.168.0.1
WEB Server on LAN side = 192.168.0.10
Mikrotik IP POOL for LAN DHCP = 10.0.0.1/8
Mikrotik IP POOL for PPPoE Users = 172.16.0.0/16
Let’s Start ….
# Syed Jahanzaib / aacable@hotmail.com # https://aacable.wordpress.com # Adding IP pool for dhcp and pppoe /ip pool add name=pppoe-pool ranges=172.16.0.1-172.16.1.255 add name=dhcp_pool ranges=10.0.0.1-10.0.0.255 # ADD dhcp server /ip dhcp-server add address-pool=dhcp_pool authoritative=after-2sec-delay bootp-support=static disabled=no interface=Local lease-time=6h name="ZAIB DHCP SERVER" /ip dhcp-server config set store-leases-disk=5m /ip dhcp-server network add address=10.0.0.0/8 comment="zaib DHCP SERVER" dhcp-option="" dns-server=192.168.0.1,8.8.8.8 gateway="" ntp-server="" wins-server="" # Adding dsl pppoe client connections, make sure your dsl modems are in bridge mode. /interface pppoe-client add ac-name="" add-default-route=yes allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=no interface=WAN1 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out1 password=ISP_DSL_PASSWORD profile=default \ service-name="" use-peer-dns=no user=ISP_DSL_USERNAME add ac-name="" add-default-route=yes allow=pap,chap,mschap1,mschap2 dial-on-demand=no disabled=no interface=WAN2 max-mru=1480 max-mtu=1480 mrru=disabled name=pppoe-out2 password=ISP_DSL_PASSWORD profile=default \ service-name="" use-peer-dns=no user=ISP_DSL_USERNAME # Adding PPPoE Default Profile /ppp profile add change-tcp-mss=default dns-server=192.168.0.1,8.8.8.8 local-address=192.168.0.1 name=pppoe-profile only-one=yes rate-limit=512k/512k remote-address=pppoe-pool use-compression=default use-encryption=no \ use-mpls=default use-vj-compression=default # Adding PPPOE Server /interface pppoe-server server add authentication=pap default-profile=pppoe-profile disabled=no interface=Local keepalive-timeout=10 max-mru=1480 max-mtu=1480 max-sessions=0 mrru=disabled one-session-per-host=no service-name=service1 # Create address list and add your users pppoe pool and web server ip addresses in this list, later we will use this list as ACL to allow specific users internet access /ip firewall address-list add address=172.16.0.1-172.16.1.255 comment="Allowed Users to Use Internet" disabled=no list="allowed users" add address=192.168.0.10 comment="Allowed Users to Use Internet" disabled=no list="allowed users" # Now start Mangling /ip firewall mangle ############################################ > Zaib # PORT FORWARDING RELATED MANGLE SECTION STARTS ############################################ # This section is related to packet marking for Marking connections/packets arrived at WAN1 link add action=mark-connection chain=input comment="Mark Connection - IN wan1,OUT wan1 Syed.Jahanzaib" disabled=no in-interface=pppoe-out1 new-connection-mark=pppoe_out1_conn passthrough=yes add action=mark-routing chain=output comment="Mark Routing - IN wan1,OUT wan1" connection-mark=pppoe_out1_conn disabled=no new-routing-mark=pppoe_out1_traffic passthrough=no # This section is related to packet marking for Marking connections/packets arrived at WAN2 link add action=mark-connection chain=input comment="Mark Connection - IN wan2, OUT wan2" disabled=no in-interface=pppoe-out2 new-connection-mark=pppoe_out2_conn passthrough=yes add action=mark-routing chain=output comment="Mark Routing - IN wan2,OUT wan2" connection-mark=pppoe_out2_conn disabled=no new-routing-mark=pppoe_out2_traffic passthrough=no add action=mark-connection chain=forward comment="Mark Connection for new conn - Packet Forward wan1, out wan1" connection-state=new disabled=no in-interface=pppoe-out1 new-connection-mark=pppoe_out1_pfw \ passthrough=no add action=mark-routing chain=prerouting comment="Mark Packets for new conn - Packet Forward wan1, out wan1" connection-mark=pppoe_out1_pfw disabled=no in-interface=Local new-routing-mark=\ pppoe_out1_traffic passthrough=no add action=mark-connection chain=forward comment="Mark Connection for new conn - Packet Forward wan2, out wan2" connection-state=new disabled=no in-interface=pppoe-out2 new-connection-mark=pppoe_out2_pfw \ passthrough=no add action=mark-routing chain=prerouting comment="Mark Routing for new conn - Packet Forward wan2, out wan2" connection-mark=pppoe_out2_pfw disabled=no in-interface=Local new-routing-mark=\ pppoe_out2_traffic passthrough=no ######################## # GENERAL PCC SECTION ######################## # This section is related to packet marking for general PCC add action=accept chain=prerouting disabled=no in-interface=pppoe-out1 add action=accept chain=prerouting disabled=no in-interface=pppoe-out2 # Classifier for dual WAN links add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan1_conn passthrough=yes per-connection-classifier=src-address:2/0 src-address-list="allowed users" add action=mark-connection chain=prerouting disabled=no dst-address-type=!local new-connection-mark=wan2_conn passthrough=yes per-connection-classifier=src-address:2/1 src-address-list="allowed users" add action=mark-routing chain=prerouting connection-mark=wan1_conn disabled=no new-routing-mark=to_wan1 passthrough=yes src-address-list="allowed users" add action=mark-routing chain=prerouting connection-mark=wan2_conn disabled=no new-routing-mark=to_wan2 passthrough=yes src-address-list="allowed users" ########################################################## # NAT / DST-NAT / MASQUERADE SECTION / PORT FORWARD ########################################################## /ip firewall nat ### Route WEB Port from wan links to local web server IP/PORT add action=dst-nat chain=dstnat comment="Route WEB Server Port 80 from INTERNET LINK1" disabled=no dst-port=80 in-interface=pppoe-out1 protocol=tcp to-addresses=192.168.0.10 to-ports=80 add action=dst-nat chain=dstnat comment="Route WEB Server Port 80 from INTERNET LINK2" disabled=no dst-port=80 in-interface=pppoe-out2 protocol=tcp to-addresses=192.168.0.10 to-ports=80 ### Allow internet access/masquerade to allowed users list only (ACL) add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out1 src-address-list="allowed users" add action=masquerade chain=srcnat disabled=no out-interface=pppoe-out2 src-address-list="allowed users" ################################################## # ROUTE SECTION FOR PCC AND PORT FORWARD PACKETS ################################################## # Add routes for general PCC /ip route add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 routing-mark=to_wan1 scope=30 target-scope=10 add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=pppoe-out2 routing-mark=to_wan2 scope=30 target-scope=10 # Add routes for IN/OUT port forwarding packets add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out1 routing-mark=pppoe_out1_traffic scope=30 target-scope=10 add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=pppoe-out2 routing-mark=pppoe_out2_traffic scope=30 target-scope=10
Regard’s
Syed Jahanzaib




why are you playing this script sir !
LikeLike
Comment by 3l1t3p0is0n — March 30, 2015 @ 2:11 PM
salam,
jahanzaib bhai please can u explain about connect internet and fariya internet?
kya mien apna aisa setup bana sakta hun mikrotik par jese connect ka network for examples.
dhcp server with classless route
dns servers
and pptp servers
bridge gateway
miene dhcp-server with classless route bana liya..
dns server bhi bana liya
pptp server bhi banaliya
lekin bridge gateway kese banaon connect ka vlan hai ya bridge hai?
connect ka support after gateway local users ip’s ka remote kese leleta hai…radius panel mien bhi jo users
connect par connected hote hain unki local ips alag alag aati hain jo dhcp assign karta hai… please meri help kijeye.mujhe bhi aisa setup banana hai khud k liye please….. reply.
LikeLike
Comment by waqas hussain — March 30, 2015 @ 2:54 PM
can i follow this method for my cctv ?
LikeLike
Comment by faizrazak — March 30, 2015 @ 3:21 PM
Asallam-o-Alaikum Syed Jahanzaib Bahi kesay hain ap Allah Ap ko Hamesha khush rakhe ap bohat acha kam karte hain logo ki help kar k….bahi menay hotspot with pppoe server banaya howa hai problem yeh hai k jab hotspot wale user https://www.google.com try karte hain to login page nahi ata or agar http://www.google.com.pk try karo to ajat hai matlab k https redirect nahi hoti login page par is ka koe hal to btayein please Q k har client ziyada try https://www.google.com hee try karte hain ab har client ko btana parta hai bari mushkil hojati hai please koe hal to btayein is ka….. Mujhe intazar rahe ga ap k reply ka
Best Regards
Jalil abbas
LikeLike
Comment by Jalil Abbas — March 31, 2015 @ 4:56 PM
Reblogged this on SUMONCHAI and commented:
ทดสอบแล้ว ใช้งานได้ดี เลย
เข้า Dnat ทางใหน ออกทางนั้น
LikeLike
Comment by LAO — April 1, 2015 @ 8:44 AM
Hello, syed, I love your flipflops, to implement this rolling, I found some inconsistencies.
first:
Remain at zero, the traffic is not sent, besides the _pfw traffic is not used at any time.
new-routing-mark is rewritten?
add action = mark-connection chain = forward comment = “Packet Forward WAN1, WAN1 out” connection-state = new disabled = no in-interface = pppoe-out1 new-connection-mark = pppoe_out1_pfw passthrough = no
add action = mark-routing chain = prerouting comment = “Mark WAN1, WAN1 out” connection-mark = pppoe_out1_pfw disabled = no in-interface = Local new-routing-mark = pppoe_out1_traffic passthrough = no
add action = mark-connection chain = forward comment = “Mark wan2, wan2 out” connection-state = new disabled = no in-interface = pppoe-out2 new-connection-mark = pppoe_out2_pfw passthrough = no
add action = mark-routing chain = prerouting comment = “Mark wan2, wan2 out” connection-mark = pppoe_out2_pfw disabled = no in-interface = Local new-routing-mark = pppoe_out2_traffic passthrough = no
because deploy.
per-connection-classifier = src-address: 2/0
and why not implement?
per-connection-classifier = both-addresses-and-ports: 2/0
route?
/ Ip route
add check-gateway = ping disabled = no distance = 1 dst-address = 0.0.0.0 / 0 = pppoe-out1 gateway routing-mark = to_wan1 scope = 30 target-scope = 10
add check-gateway = ping disabled = no distance = 2 dst-address = 0.0.0.0 / 0 = pppoe-out2 gateway routing-mark = to_wan2 scope = 30 target-scope = 10
# Add routes for IN / OUT port forwarding packets
add disabled = no distance = 1 dst-address = 0.0.0.0 / 0 = pppoe-out1 gateway routing-mark = wan1_conn scope = 30 target-scope = 10
add disabled = no distance = 1 dst-address = 0.0.0.0 / 0 = pppoe-out2 gateway routing-mark = wan2_conn scope = 30 target-scope = 10
Only these rules do not exist ?, conditional, for other rules.
LikeLike
Comment by cyberjzus — April 1, 2015 @ 5:41 PM
thanks a lot for your great tutorials
if you can tweak the configuration to make it possible for pptp on the router board itself
LikeLike
Comment by Ahmed Gamal — April 3, 2015 @ 5:15 PM
Sir how to bypass queue limit just “facebook”
Site on mikrotik…..
Allah aap ko jaza e khair dey
LikeLike
Comment by Salman — April 23, 2015 @ 9:51 PM
I have a CCR1036 with PPPoE Server and HotSpot Server enabled. I also have 10 vdsl lines installed on it. I’m looking for a working PCC Load Balace script, which will balance all 10 lines for both pppoe clients and hotspot clients.
I’ve done some tests but I only managed to balance either hotspot clients or pppoe clients. I didn’t manage to balace the traffic of both of them.
Any ideas?
Thanks in advanced.
LikeLike
Comment by markpap — May 27, 2015 @ 1:54 AM
Dear Sir. in my case i do have eth3, 4, 5 for LAN instead of local. how do i add that?
LikeLike
Comment by john — June 30, 2015 @ 6:31 PM
We totally confused to why our hotspot breaks when we turn on use-ip-firewall-for-vlan=yes. If we set use-ip-firewall-for-vlan=no our PCC load balancing does not work.
My setup is the following:
Hardware:
Mikrotek CCR1009-8G-1S v6.32.3
UniFi AP-AC-Pro & UniFi AP-AC Outdoor using Controller v4.76.
UniFI Toughswitch POE
WLANS (3 Internet Connections)
We have 3 SSID setup using VLAN:
Team (On Bridge 192.168.10.0)
Hotspot (VLAN20)
Members (VLAN30)
VLANs are correctly setup on the Unifi controllers and everyone is being assigned the correct DHCP. We have tested many different scenerios however when we enable the “use-ip-firewall-for-vlan=yes” it blocks the hotspot from loading the browser just hangs and no login box appears. If we type in the router IP normaly it would load the hotspot in this case it just loads the routeros admin interface. Further wierdness, if we put a website in the wall garden ip list, we can get to this website. So the issue is the hotspot just doesn’t display or its not fowarding the connection.
Not that its really relevant but we are using PCC for load balancing and this only works when we “use-ip-firewall-for-vlan=yes” the load balancing works perfectly, we thought this could be effecting loading the hotspot. So we reset the router with a fresh configuration (see configuration below) with just a simple route and tested it with out load balancing and the same thing happens. If we switch the rule to “use-ip-firewall-for-vlan=no” then bang the hotspot works perfectly!!!
What is happening? Do we need another rule setup?
LikeLike
Comment by Dojo Mike — December 2, 2015 @ 3:19 PM
Here are what the different field options mean for the purpose of packet matching, these are the fields that will be fed into the hashing algorithm (and, for the purpose of spreading load across links, decide what link a packet will be put on). Remember that a hash function will always produce the same input when it’s fed the same output:
src-address: The source address of a client will always be the same, so all traffic from a particular client will always match the same PCC matcher, and will always be put on the same link.
dst-address: The destination address of a specific server will always be the same, so all traffic to that server (say, the Mikrotik Wiki) will always match the same PCC matcher, and will always be put on the same link.
both-addresses: The source and destination IP pair between the same client and server will always be the same, so all traffic between one specific client and a specific server (say, your laptop and the Mikrotik Wiki) will always match the same PCC matcher, and will always be put on the same link.
src-port: Source ports of clients are usually randomly chosen when the connection is created, so across many connections different source ports will be fed into the hash function, and different PCC matchers will match and traffic will go across different links. However, some client protocols always choose the same source port, and servers behind your router will mostly likely always use the same service port to send traffic back to their clients. A web server behind your router would send most traffic from its HTTP (80) and HTTPS (443) ports, and that traffic would always match the same PCC matcher and would be put on the same link.
dst-port: Destination ports of clients are usually well defined service ports, all HTTP (80) traffic between your clients and servers on the Internet would always match the same PCC matcher, and would be put on the same link. However, the same clients doing HTTPS (443) traffic could match a different PCC matcher, and would go across a different link.
both-ports: Since the client port is (usually) randomly chosen, the combination of the two ports is (usually) random and will spread load across links.
src-address-and-port: Same caveat as src-port.
dst-address-and-port: Same caveat as dst-port.
both-addresses-and-ports: This is the most random way to spread traffic across links, since it has the most number of variables.
LikeLike
Comment by kashif khan — February 11, 2016 @ 3:14 PM
[…] Source: Playing with the Mikrotik’s PCC | Syed Jahanzaib Personal Blog to Share Knowledge ! […]
LikeLike
Pingback by URLs for Mikrotik PCC load balancing « The Wiert Corner – irregular stream of stuff — June 16, 2017 @ 4:01 PM
Thanks Sir! You have solved load balancing with port forwarding of two ISP’s, I joint this script with dst nat port forwarding of two static ip ISP’s and this works like a charm!. There are lot of scripts on Internet which works perfectly with load balancing but not with port forwarding. By adding mangle rules of Port Forwarding , It works perfectly. My name is Neeraj Kakar , Iam from India. Thanks Again!
LikeLike
Comment by semispare — January 2, 2022 @ 9:38 PM
Welcome
LikeLike
Comment by Syed Jahanzaib / Pinochio~:) — January 24, 2022 @ 2:27 PM