

Disclaimer:
Every Network is different , so one solution cannot be applied to all. Therefore try to understand logic & create a solution that can match with your network scenario. Do not follow copy paste blindly.
I am NOT certified in anything Mikrotik/Cisco/Linux or Windows. However I have worked with some core networks and I read & research & try stuff all of the time. So I am not speaking/posting about stuff I am formerly trained in, I pretty much go with experience and what I have learned on my own. And , If I don’t know something then I read & learn all about it.
So , please don’t hold me/my-postings to be always 100 percent correct. I make mistakes just like everybody else. However – I do my best, learn from my mistakes and always try to help others
Regard’s
Syed Jahanzaib
Scenario:
We are using Mikrotik CCR as PPPOE NAS. It’s a mix match scenario where large number of users receive private ip (via pppoe connection) and smaller number of users gets public ip (routed Public pool)
Problem:
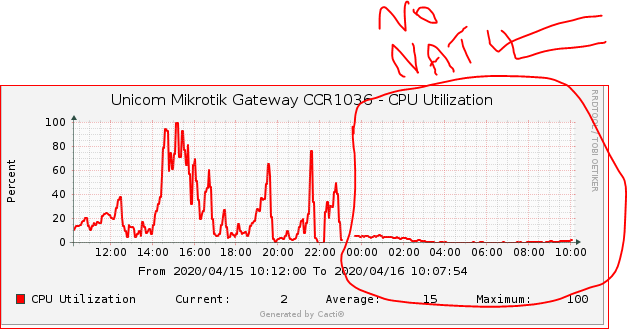
When we have network outages like light failure in any particular area OR port flaps, in LOG we can see many PPPoE sessions disconnects with ‘peer not responding‘ messages. Exactly at this moments, our NAS CPU usage reaches to almost 100% , which results in router stops passing any kind of traffic. This problem continues for 2-3 minutes.
As shown in the image below …

After lurking in the mikrotik forums, I was informed that If you are using Masquarade /NAT on the router, that is the problem. When using Masquarade, RouterOS has to do full connection tracking recalculation on EACH interface connect/disconnect. So if you have lots of PPP session connecting/disconnecting, connection tracking will constantly be recalculated which can cause high CPU usage. When interfaces connect/disconnect, in combination with NAT, it gives you high CPU usage.
Solution OR Possible Workaround :
- If you have lots of PPP users along with some NATTING rules, Stop using Masquarade on same router that have a lot of dynamic interfaces. DO NOT use NAT on any router that have high number of connecting/disconnecting interfaces , like pppoe/vpn. Place an additional router connected with your PPPoE NAS, and route NAT traffic there. Make sure to disable CONNECTION TRACKING on PPPoE NAS router.
Example: Add another router & perform all natting on that router by sending marked traffic from private ip series to that nat router. Setup routing between the PPPoE NAS and the NAT router.Make sure to disable CONNECTION TRACKING on PPPoE NAS router.
Following is an working example.
1# Main CCR as PPPOE NAS
Interface Details:
- ETHER1-LAN-: 192.168.88.1/24 < User facing interface where pppoe connections establishes. Consider it as LAN facing side for pppoe users.
- PUBLIC-WAN: 101.11.11.254 < WAN Interface for public IP routing
- 2-NAT-ROUTER: 192.168.100.2/24 < interface connected with another CCR for natting traffic routing
- PPPoE User IP Pool > 172.16.0.1-172.16.0.255
- UPSTREAM ISP Core Router Gateway IP > 101.11.11.36
2# Second CCR as NATTING Router
Interface Details:
- 2nd-NAT-CCR-LAN: 192.168.100.1/24 < interface connected with main CCR [for pppoe users traffic]
- NATTING-WAN: 101.11.11.253 < Wan interface for natting users [traffic coming from main CCR for natting]
- UPSTREAM ISP Core Router Gateway IP > 101.11.11.36
- PPPoE Users Pool – 172.16.0.0/24
1# Main CCR Configuration for marking traffic
First we will mark traffic for private/public ip and will create routes for them as well.
/ip firewall mangle add action=mark-routing chain=prerouting comment="Mark routing for Private IP users - zaib" disabled=no new-routing-mark=nat_routing passthrough=yes src-address=172.16.0.1-172.16.0.255 # We really dont need to mark traffic for public ip's because they will simply pass from our default route , but just for the sake of demonstration we are doing it. add action=mark-routing chain=prerouting comment="Mark routing for PUBLIC IP users - zaib" disabled=no new-routing-mark=public_routing passthrough=yes src-address=1.1.1.1-1.1.1.255Make sure you dont have any NAT rule in place. [in NAT section]
Now add Routes for marked traffic
/ip route add comment="Route private ip traffic via second NAT router" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.100.1 routing-mark=nat_routing scope=30 target-scope=10 add comment="Route public ip via this router default Gateway" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=101.11.11.36 routing-mark=public_routing scope=30 target-scope=10 # DEFAULT Gateway for router's own traffic - zaib add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=101.11.11.36 scope=30 target-scope=10Main CCR configuration part is done. Now moving towards second router where all NATTING will be done.
2# NATTING CCR Configuration for Masquerade
First create Default NAT rule [you may want to add ip series for security purposes.
/ip route add comment="Default Router for NATTING router " disabled=no distance=1 dst-address=0.0.0.0/0 gateway=101.11.11.36 scope=30 target-scope=10 # Add reverse Route so that NATTING router can see the pppoe user directly add disabled=no distance=1 dst-address=172.16.0.0/16 gateway=192.168.100.2 scope=30 target-scope=10
Testing !
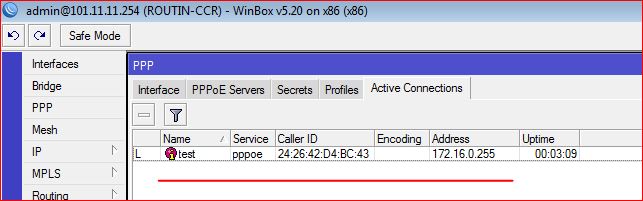
- Create TEST user in main CCR pppoe NAS,
- Assign him private ip series profile,
- Connect this TEST id from test PC & run TRACEROUTE
As shown in the image below …
.

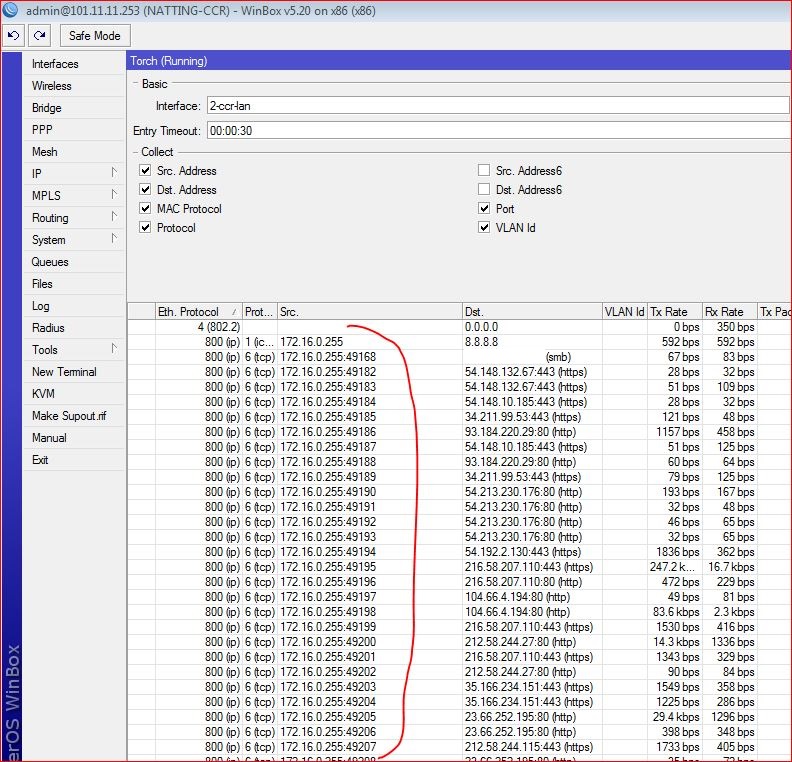
RUN Torch on NATTING Router… as we can see that NATTING router is seeing pppoe users directly dueto reverse route in it.
Final Step.
Once you have routed all private ip series 2 2nd CCR, Make sure to disable CONNECTION TRACKING on the pppoe router (1st router where users are connected via pppoe) by using cmd
/ip firewall connection tracking set enabled=no
Now look at the difference Before Vs After